Secure communications: end-to-end encryption (E2EE)

End-to-end encryption is a message encryption method based on asymmetric encryption algorithms and the decentralization of cryptographic keys.
Is an encrypted communication system in which only people who are communicating can read messages – or have access to shared files.
Thanks to this system, intermediaries are not allowed access to the encryption keys, thus avoiding attempts to monitor or alter the messages exchanged.
End-to-end encryption, origins and development
Starting with the basics, cryptography is the science that studies how to modify a message to make it understandable only to those who know the encryption method.
Man has always sought and invented methods to communicate securely and secretly. The oldest and simplest method of encryption is called symmetric encryption: two people use the same code (“key”) to encrypt and decrypt the messages they exchange.
However, if we refer to the IT field, symmetric cryptography proves to be quite weak. As complex as the encryption key may be, it can still be intercepted and stolen.
To overcome this problem, in 1976 Whitfield Diffie and Martin Hellman invented an alternative method, called asymmetric cryptography.
In this case, the two people communicating are not using just one key, but two pairs of keys: one public and one private. The public pair may not be protected, because security depends on the private key pair.
The operation is as follows: Elisa wants to send a message to Carlo, Elisa encrypts the message with Carlo’s public key, Carlo receives and decrypts the message with his private key.
Messages can only be decrypted with the private key corresponding to the public key that was used for encryption.
End-to-end encryption goes a step further: to increase the security of conversations, the system that manages the communication channel does not control the creation of private keys, which are generated and stored directly on the devices of the people who communicate.
For this reason, this encryption method is called end-to-end: only interested people can decrypt the messages and the communication flow does not involve third parties.
End-to-end encryption limitations
End-to-end encryption is very secure, but not foolproof. In fact, there are no foolproof security systems.
If a hacker cannot decrypt a message encoded with end-to-end encryption, he can access conversations in other indirect ways.
For example, he can use social engineering techniques to access the storage account where the user saves the conversations backup.
Or can infect the device with a keylogger, a virus that records keyboard input.
Security is a concept to be understood not as an absolute (secure or unsafe), but as a gradual one: a system is more or less secure according to the levels of security we add to it.
From this point of view, applying end-to-end encryption to instant messaging services is a big step forward.
Similarly, a correct application of security awareness best practices is also functional (if not absolutely essential) to close the security circle: in cybersecurity, it is the people’s behavior that makes the difference.
TelsyInTouchApp & Phone
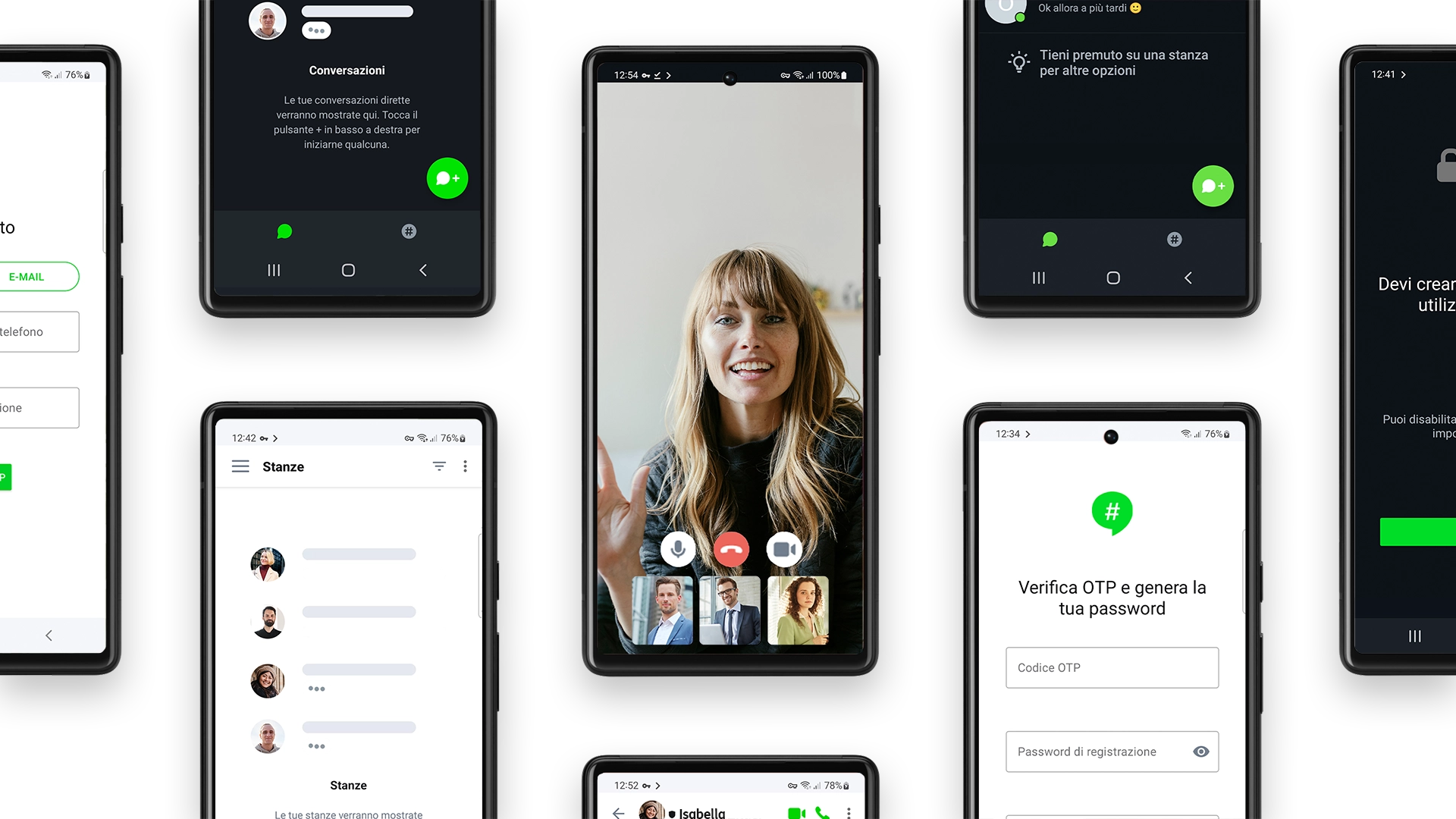 Thanks to more than fifty years of experience gained in the cryptography sector, Telsy has continued to design, innovate and develop ultra-secure technologies which led to the creation of TelsyInTouch, a dual solution that consists of two elements:
Thanks to more than fifty years of experience gained in the cryptography sector, Telsy has continued to design, innovate and develop ultra-secure technologies which led to the creation of TelsyInTouch, a dual solution that consists of two elements:
TelsyInTouchApp
An instant messaging solution that provides an unencrypted user experience similar to commercial solutions, featuring high audio and video quality thanks to the use of advanced codecs. Both for Android and iOS, TelsyInTouchApp uses end-to-end encryption for chat, VoIP calling, and audio conferencing.
TelsyInTouchPhone
TelsyInTouchPhone technology adopts a hardened platform for next-generation smartphones, able to protect devices from any external intrusion. The secure smart card is certified as root of trust and the local infrastructure and provides unconditional security.
To meet the growing need for secure communications from mobile devices, TelsyInTouchPhone allows users to share sensitive, critical, or confidential information without the need to rely on a third party.
With entirely proprietary technologies and an on-premise ecosystem, TelsyInTouch is a communication tool that uses end-to-end encryption, created to offer uncompromising security allowing you to share confidential information while maintaining the same traditional communication apps usability.
Discover our Secure Communications solutions.
