CRYPTO
Telsy represents a national flagship in communications security. Thanks to over 50 years of experience and tireless research, Telsy’s cryptographic systems guarantee the highest standards of security in data transfer and communications.
The integration between cryptographic solutions and cybersecurity services, accompanied by high-profile experts, makes Telsy’s Crypto portfolio a pool of expertise capable of offering cutting-edge proprietary products and algorithms, developing systems capable of protecting communications to meet evolving threats.
Speed, reliability, efficiency. These are the imperatives in today’s communications security landscape. Protecting our data from theft and tampering is increasingly complex and requires tools that are up to the task.
With its historical expertise in developing proprietary ciphers and algorithms, Telsy ensures maximum protection in the transfer of data and communications, providing articulations for government and defense in support of national security.
Layer 3 encryptor for the protection of unclassified communications, with a throughput of 1 Gb/s. Available in Rack and Desktop versions.
Learn more in the brochure.
For further information contact@telsy.it

Our private and professional conversations are constantly at a security risk. Telsy offers systems for collaboration and information sharing among multiple users through a variety of means, enabling legitimate owners to maintain full control over information with simple and efficient solutions.
Web conference platform that uses asymmetric encryption protocols to secure participant authentications, ensuring full control and security of communications.
Learn more in the brochure.
For further information contact@telsy.it
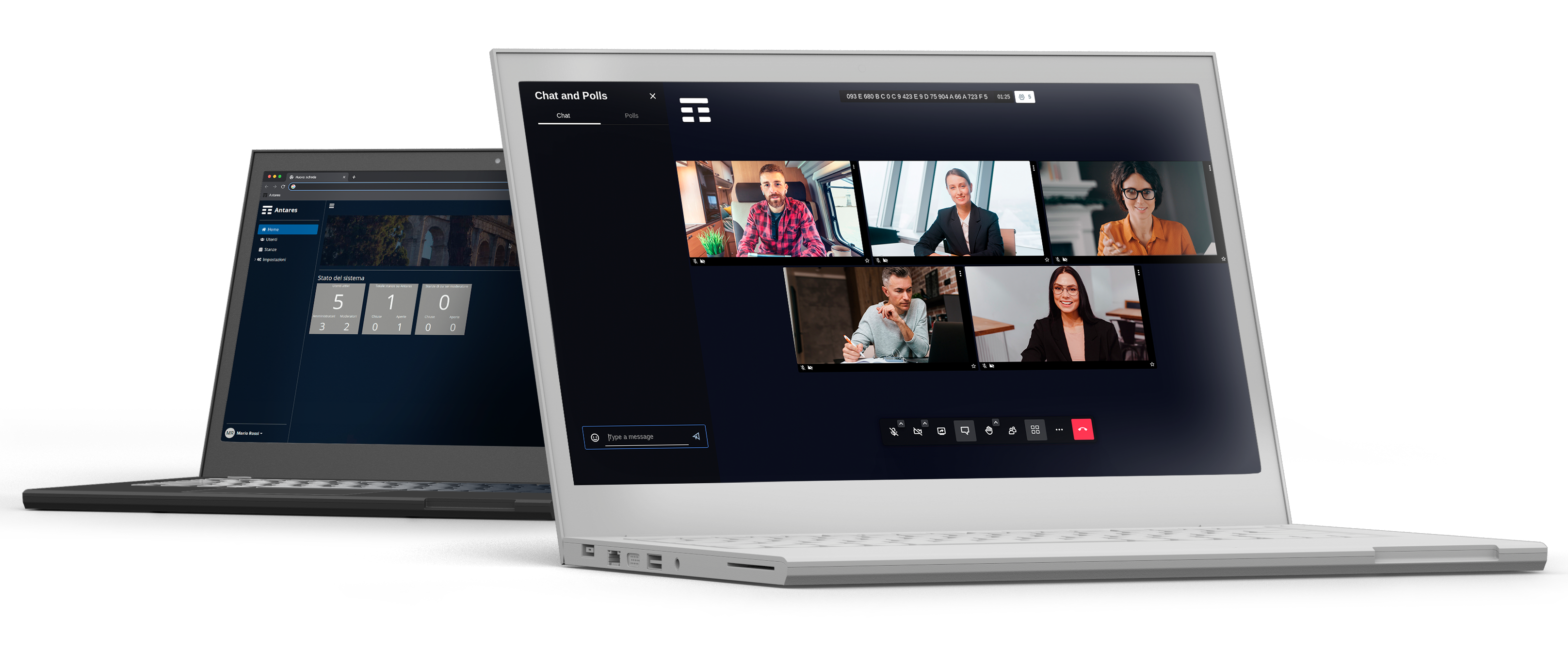
TelsyInTouch is an innovative dual and integrated Secure Collaboration solution that consists of two distinct interoperating elements:
TelsyInTouchApp – Secure messaging application
TelsyInTouchPhone – Hardened phone certificated common criteria 3.1 and 2
Learn more in the brochure.
For further information contact@telsy.it

An ultrasonic audio jammer that inhibits recording by malicious applications on compromised smartphones and mobile devices.
Learn more in the brochure.
For further information contact@telsy.it

It is a VoIP cryptophone with a built-in VPN, which protects data transmitted to and from application servers embedded in the Telsy Secure Cloud System (TSCS).
The TelsyCryptophone T2 can be connected to any PC in the private network, thus extending VPN protection to the communication applications used.
Learn more in the brochure.
For further information contact@telsy.it

Contact
To learn more details about our products and solutions: contact@telsy.it
