The videoconference vulnerabilities

As for business meetings or for hearing the family from all corners of the world, many people use video conferencing to connect with others and will likely continue to do so as global digitization advances.
With millions of people around the world working from home, videoconferencing is quickly establishing itself as the new norm, representing today a convenient alternative (or aid) to many activities.
But with the rapid adoption of video conferencing apps and tools, potential vulnerabilities that can translate into threats to your online security has come out.
The most common videoconference vulnerabilities
One of the recently discussed security videoconference vulnerabilities is the intrusion of uninvited guests into virtual meetings.
How does it happen? According to Forbes, many users have posted invitation links to the meetings on their social media profiles.
The attacker can simply click on one of these links and interrupt an important conference or meeting with inappropriate content.
Make sure your data are in good hands
Communicating confidential business information quickly and privately with insecure tools can be risky.
 If a user needs to share private information with a colleague but is unable to communicate via phone or video, they may be relying on a messaging platform that does not provide end-to-end encryption, a feature that prevents third parties from seeing private messages.
If a user needs to share private information with a colleague but is unable to communicate via phone or video, they may be relying on a messaging platform that does not provide end-to-end encryption, a feature that prevents third parties from seeing private messages.
This could result in the inadvertent loss or sharing of confidential data, both personal and business.
Furthermore, failure to use a secure messaging platform could offer to hackers the opportunity to breach the victim’s data or device.
Depending on the severity of this type of breach, the victim may even be at risk of identity theft.
In this regard, learn more about our secure instant messaging app and other Secure Collaboration solutions.
How to avoid videoconference vulnerabilities
As users have grown accustomed to working from home, video conferencing tools will continue to be a necessary means for virtual communications. But how can they do it safely?
Here are some tips for securing your virtual meetings:
- Research: there are a lot of video conferencing tools online. Before downloading the first available, better inform yourself and check if it has possible security vulnerabilities. For example: does the tool use end-to-end encryption to ensure that only meeting attendees can decrypt protected content? Is the privacy policy of the chosen software suitable for your needs?
- Protect meetings with a password: to make sure that only invited attendees can join the meeting, it is a good idea to protect it with a password.
- Prevent users from taking control of the screen: this prevents unwanted users from taking control of the screen during the videoconference, with all the associated risks.
- Turn on automatic updates: an essential practice to ensure you have the latest security patches and enhancements as soon as they are released.
Antares: Telsy’s Videoconference Tool
The growing demand for videoconferencing solutions, combined with the consequent increase in the risks associated with the security of communications that pass through it, highlight the need for a solution focused on guaranteeing the security of the exchanged contents.
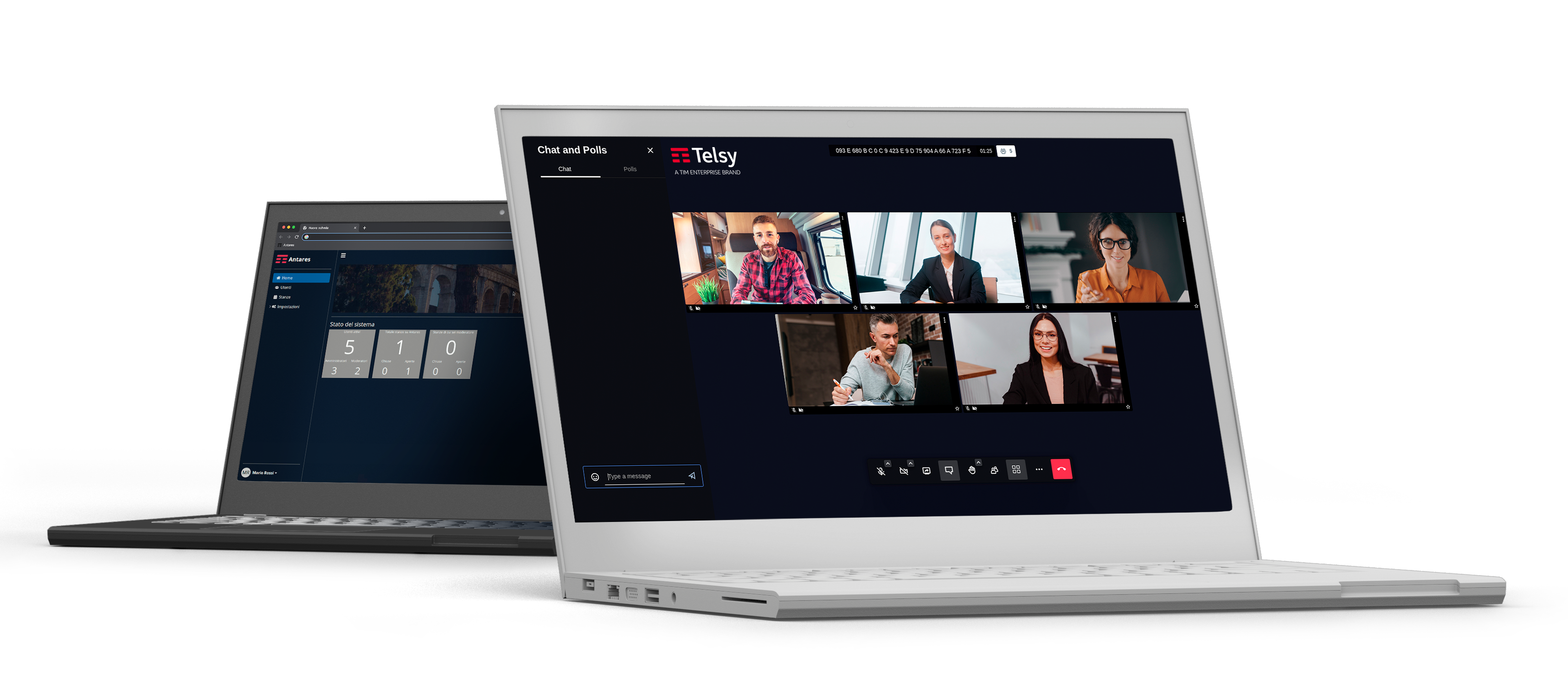 Antares is the Telsy’s proposal: a web conference platform that uses asymmetric encryption protocols to ensure participant authentication.
Antares is the Telsy’s proposal: a web conference platform that uses asymmetric encryption protocols to ensure participant authentication.
Antares is a solution developed to allow simple and quick configuration for any environment of use, ensuring security levels superior to any other video conference solution.
In fact, the cryptographic keys are held and managed exclusively by the owner of the facility, without external mediation.
Antares also allows, as an additional layer of security, the application of end-to-end encryption where the cryptographic keys are available only to the participants of the call in progress, definitively restricting the vulnerability surfaces against sniffing attacks and the like.
Antares Functionalities
Here are some of the main features and functionalities of the Antares video conferencing solution:
- Full control of the infrastructure and information through distribution on a hardware platform dedicated to the Customer and installed on-site;
- Possibility of videoconferencing with mixed traffic (traffic from internal network, traffic from external network, traffic from both internal and external network);
- Monitoring of the platform by sending logs to SIEM (syslog) or Stack ELK;
- Prevention of network intrusions through centralized user registrations management;
- Password management according to IAM best practices;
- Dashboard with platform statistics;
- Management dashboard for managing users and rooms;
- Videoconferences with no time limits and up to 50 participants;
- Use of WebRTC technology;
- Ability to activate end-to-end connection encryption mechanisms to ensure maximum privacy and communication security;
- Multi-factor authentication support;
- Most common features of videoconferencing systems.
Find out more about Antares and our other Secure Communications solutions.
