The Cyber Incident Response

Every day thousands of companies have to face the growing threat of cybercrime and Security Incidents, with consequent waste of time and money.
In the modern corporate landscape, we have witnessed an increase in the attack surface available to malicious actors, due to the digital solutions increase in companies: this circumstance cannot be ignored or underestimated and therefore companies must be ready to answer attacks by setting up an effective Incident Response (IR) plan.
To prevent cyber threats, it’s important to have an adequate defensive structure, equipped with the most modern and efficient tools, constantly updated, with the most advanced protection systems, and with educated, trained, and qualified personnel, ready to stop the initiatives of the bad guys.
The context
As in any business sector, the proactive component alone is not enough; security incidents can occur in even the most armored organizations, and therefore having a division dedicated to “reactive” behavior is equally important.
Several IT incidents are recorded every day by companies, and this trend has significantly increased in the last few years.
Furthermore, these incidents are growing in quantity and quality: according to the 2022 Clusit report, 78% of total attacks had a critical and high impact, compared to 50% in 2020.
The particularly negative scenario that emerged in 2022 is also confirmed in the first half of 2023: from 2018 to June 2023, 505 known high-severity attacks involving Italian realities were surveyed in the Report, of which as many as 132 (26%!) occurred in the first 6 months of 2023.
The Incident Response is a fundamental process within this context and, for this reason, having a team of people assigned for this purpose, suitably trained and equipped with the appropriate tools, is very important for companies.
These elements are essential since an adequately prepared environment will have the necessary strength to withstand the impact deriving from any adverse events in the cyber environment.
Incident Response: a definition
The National Institute of Standards and Technology – NIST, defines Incident Response as follows: “Incident Response is a structured process that organizations use to identify and manage information security incidents. The response includes several phases, including incident preparedness, detection and analysis of a security incident, containment, eradication, and full recovery, as well as post-incident learning and analysis.”
In this sense, having an internal specialized team allows for managing incidents in a systematic and timely way. The team responsible for handling security incidents is called Incident Response Team (IRT). Often in some organizations, this capacity is absorbed in whole or in part within the SOCs or CSIRTs and, if they do not have it, it is advisable for these organizations to entrust themselves to specialized companies equipped with the necessary infrastructures.
Incident Response Lifecycle Phases
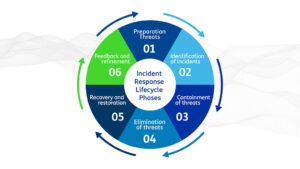
The Incident Response is a set of information security policies and procedures aimed to identify, contain, and eliminate cyber attacks.
The incident response goal is to enable an organization to quickly detect and halt attacks, minimizing damage and preventing future attacks of the same type.
There are six steps to incident response. These six steps occur in a cycle each time an incident occurs.
The steps are:
- Preparation of systems and procedures
- Identification of incidents
- Containment of attackers and incident activity
- Eradication of attackers and re-entry options
- Recovery from incidents, including restoration of systems
- Lessons learned and application of feedback to the next round of preparation
Preparation
During your first preparation phase, existing security measures and policies are reviewed to determine effectiveness.
This involves performing a risk assessment to determine what vulnerabilities currently exist and the priority of your assets.
Information is then applied to prioritizing responses for incident types. It is also used, if possible, to reconfigure systems to cover vulnerabilities and focus protection on high-priority assets.
This phase refines existing policies and procedures or writes new ones if there is a lack. These procedures include a communication plan and assignment of roles and responsibilities during an incident.
Threats Identification
Using the tools and procedures determined in the preparation phase, teams work to detect and identify any suspicious activity.
When an incident is detected, team members need to work to identify the nature of the attack, its source, and the goals of the attacker.
During identification, any evidence collected needs to be protected and retained for later in-depth analysis. Responders should document all steps taken and evidence found, including all details.
During this phase, after an incident is confirmed, communication plans are also typically initiated. These plans inform security members, stakeholders, authorities, legal counsel, and eventually users of the incident and what steps need to be taken.
Containment of threats
After an incident is identified, containment methods are determined and enacted. The goal is to advance to this stage as quickly as possible to minimize the amount of damage caused.
Containment is often accomplished in sub-phases:
- Short-term containment—immediate threats are isolated in place. For example, the area of your network that an attacker is currently in may be segmented off. Or, a server that is infected may be taken offline and traffic redirected to a failover.
- Long-term containment—additional access controls are applied to unaffected systems. Meanwhile, clean, patched versions of systems and resources are created and prepared for the recovery phase.

Elimination of threats
During and after containment, the full extent of an attack is made visible. Once teams are aware of all affected systems and resources, they can begin ejecting attackers and eliminating malware from systems.
This phase continues until all traces of the attack are removed. In some cases, this may require taking systems offline so assets can be replaced with clean versions in recovery.
Recovery and restoration
In this phase, teams bring updated replacement systems online. Ideally, systems can be restored without loss of data but this isn’t always possible.
In the latter case, teams must determine when the last clean copy of data was created and restore from it. The recovery phase typically extends for a while as it also includes monitoring systems for a while after an incident to ensure that attackers don’t return.
Feedback and refinement
The lessons learned phase is one in which the IRT reviews what steps were taken during a response.
Members should address what went well, what didn’t, and make suggestions for future improvements. Any incomplete documentation should also be wrapped up in this phase.
What is an Incident Response Plan (IRP)?
An incident response plan is a document that outlines an organization’s procedures, steps, and responsibilities of its incident response program.
Incident response planning often includes the following details:
- how incident response supports the organization’s broader mission
- the organization’s approach to incident response
- activities required in each phase of incident response
- roles and responsibilities for completing IR activities
- communication pathways between the incident response team and the rest of the organization
- metrics to capture the effectiveness of its IR capabilities
It’s important to note that an IR plan’s value doesn’t end when a cybersecurity incident is over; it continues to provide support for successful litigation, documentation to show auditors, and historical knowledge to feed into the risk assessment process and improve the incident response process itself.
TelsyIncidentResponse: Telsy’s proposal
 TelsyIncidentResponse is the service that allows you to have direct contact with professionals dedicated to providing operational and forensic support to companies that have suffered data breaches and/or IT incidents, in order to share the indications and countermeasures to be implemented to restore business continuity.
TelsyIncidentResponse is the service that allows you to have direct contact with professionals dedicated to providing operational and forensic support to companies that have suffered data breaches and/or IT incidents, in order to share the indications and countermeasures to be implemented to restore business continuity.
The service, active 24/7, is aimed at customers who require immediate support, allowing them to get in touch directly with Telsy’s iSOC by dialing the number 800.811.822 and entering the pin 1971.
An operator will collect the information needed to activate Telsy’s Incident Response Team and proceed with assistance activities for restoring the correct functioning of the services impacted by the incident.
Find out all Telsy’s cybersecurity solutions.
