CYBER
Telsy is the TIM Group’s competence center in cybersecurity and cyber resilience for the government and civilian markets. Always on the front lines against cybercrime, Telsy provides its expertise to assess corporate security levels and address the most complex threats, ensuring the highest quality and efficiency in every situation.
Telsy offers advanced, integrated, scalable, and customizable cybersecurity-as-a-service solutions, based on proprietary computing platforms and highly skilled experts, to build and enhance a defense strategy tailored to the client’s needs.
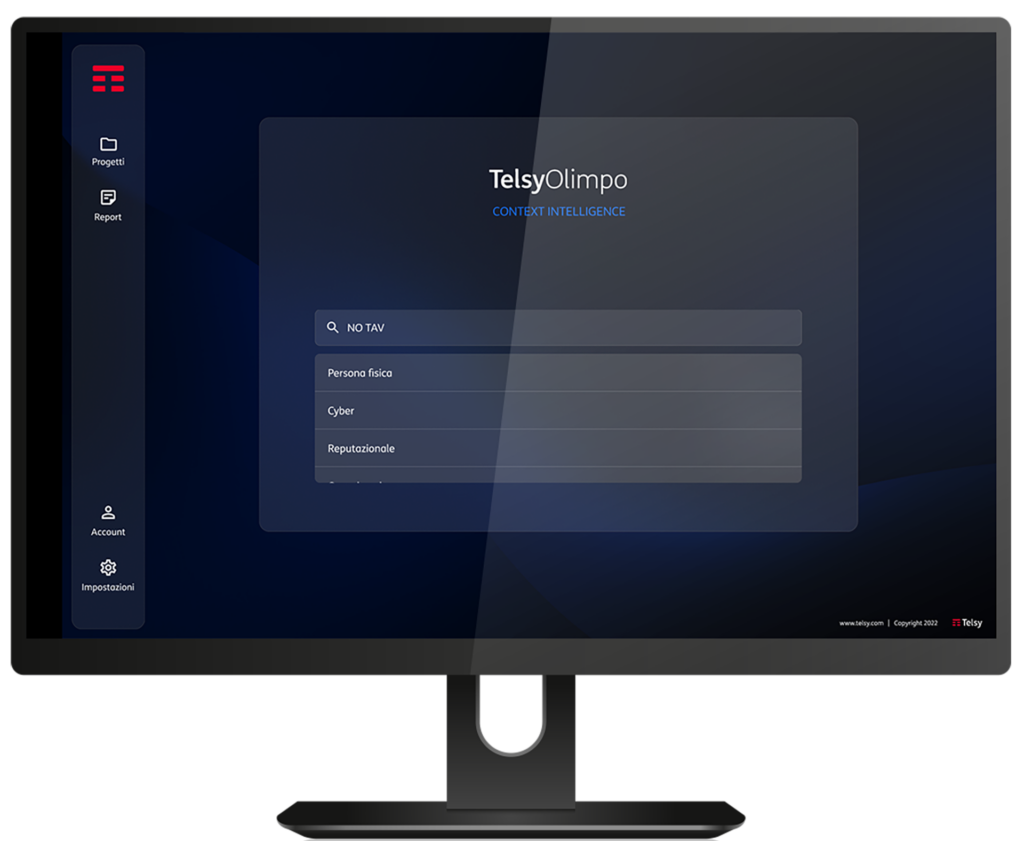
Telsy’s Decision Intelligence service, offered through the TelsyOlimpo platform, enables real-time integration and processing of data from heterogeneous sources, such as OSINT and SOCMINT, to optimize decision-making while automating often time-consuming analytical processes.
One of the specific operational contexts of TelsyOlimpo is VIP Digital Protection, a module designed specifically to provide a comprehensive overview of all data that could be actively exploited by a hypothetical threat actor to cause personal harm.
Learn more in the brochure.
For further information contact@telsy.it
The best way to prevent an attack is to test your infrastructure so as to understand its vulnerabilities and build appropriate crisis response initiatives.
Telsy provides its technologies and experts to offer quality and efficiency, preventing possible crises and providing the highest level of advice and support for user defense strategies.
For any organization, understanding the current state of its security posture requires an ongoing assessment of the risks to which it is exposed, security standards, and current cyber regulations.
Through its Cyber Risk Management services, Telsy supports companies by providing useful tools for an all-inclusive assessment of the risk exposure degree for information and technology assets, and the implementation of sustainable and effective remediation plans.
For further information contact@telsy.it
An individual’s activities in his or her interaction with the Web can put his or her security, that of the organization of which he or she is a part, and the entire supply chain at risk.
Telsy provides platforms, tools, and trainers to make employees more aware when using the Web.
Learn about Cyber Awareness & Training services on the dedicated brochure:
For further information contact@telsy.it
ICT infrastructure monitoring involves collecting and analyzing useful information to detect suspicious behavior, threats, or unauthorized system changes, enabling organizations to take countermeasures as needed.
 In cybersecurity, the proactive component alone is not enough.
In cybersecurity, the proactive component alone is not enough.
Security incidents can occur in even the most armored of facilities; therefore, having a division dedicated to “reactive” behavior is extremely important.
Telsy’s Cyber Incident Response solutions provide operational and forensic support for organizations to respond to detected threats and quickly restore business operations.
Learn more in the brochure.
For further information contact@telsy.it
Dedicated solutions for 24/7 continuous monitoring of ICT infrastructure.
Allows you to benefit from the specialized skills of Telsy’s Security Operation Center (SOC), reducing detection and response time in case of anomalies or intrusions.
Learn about Security Monitoring services on the dedicated brochures:
- iSOC Security Monitoring & Response
- TelsyDefenX
For further information contact@telsy.it
Telsy’s suite provides technologies and operational capabilities in the analysis and management of attack campaigns.
This evidence can be used to support decisions regarding prevention and response to the most advanced cyber risks.
Learn more about Treat Intelligence services in dedicated brochures.
For further information contact@telsy.it
Protection against external threats to your infrastructure comes through the use of special software, protocols, and actions capable of recognizing specific cyber attacks and blocking them.
Using state-of-the-art, proprietary, and certified technologies, Telsy protects government and corporate users’ devices and networks according to their specific needs.
Through its managed solutions offering, Telsy proposes proactive and reactive monitoring, protection, and response services for endpoints, from workstations to servers, which aims to prevent or promptly respond to cyber threats that have arrived from outside or inside, such as ransomware and phishing.
Learn about Endpoint Security services on the dedicated brochure:
For further information contact@telsy.it
The Network Security offering proposed by Telsy provides managed, modular, and highly customizable logical perimeter security solutions for small and large companies, protecting corporate networks from potential attacks from the outside through the implementation of secure connections, such as Firewalls, VPN, and Web Content Filtering.
Learn about Network Security services on the dedicated brochure:
For further information contact@telsy.it
It includes all those services or products that aim to safeguard the security of an enterprise application’s source code, the protection of data managed by the application, and the prevention of any vulnerabilities that can be exploited by malicious actors.
Activities include continuous monitoring and improving the security of enterprise applications to prevent the entry of new cyber threats.
For further information contact@telsy.it
With the growth of remote work and BYOD and CYOD policies, mobile devices have become an indispensable tool for businesses, which has expanded the perimeter to be defended and the risks to be prevented to avoid harm.
Mobile Security solutions developed by Telsy are dedicated to monitoring and protecting mobile devices to reduce the perimeter of risk to which the company could be exposed.
Learn about Mobile Security services on the dedicated brochures:
For further information contact@telsy.it
Solutions for protecting industrial automation systems that may involve infrastructure, such as hospital facilities, power plants, oil and gas refineries, manufacturing plants, or transportation infrastructure, from possible cyber threats, as well as managing the associated risks to information security and continuity of operations.
For further information contact@telsy.it
Services and solutions dedicated to the security of hospitals and healthcare infrastructures that make use of IT, OT, IoT and MiOT technologies.
In an industry where a cyber vulnerability results in a financial loss and may also cause a fatal incident, with consequent legal and reputational damage, it is critical to ensure constant protection against different types of threats.
For further information contact@telsy.it
Contact
To learn more details about our products and solutions: contact@telsy.it
