Risk Analysis and VAPT: how to manage cyber risk

Companies and organizations are constantly looking for ways to protect their data and online activities from cyber risk.
The inescapable use of the Web and new ways of collaboration have accelerated this trend dramatically, and today there quite difficult in keeping up.
Among the tools that can be used to protect against online dangers, there are VAPT (Vulnerability Assessment and Penetration Testing) and Risk Analysis procedures.
Vulnerability Assessment and Penetration Testing (VAPT)
VAPT is a process that consists of the assessment of information system vulnerabilities, followed by the simulation of a cyber attack to evaluate the effectiveness of security countermeasures.
The goal of VAPT is to identify system vulnerabilities and suggest corrective actions to eliminate them. VAPTs are often used by companies to improve the security of their computer systems and reduce the risk of attacks.
VAPT can be performed in a variety of ways. For example, specific procedures or vulnerability scanning software can be used to identify possible system flaws, such as open ports or out-of-date software. Good practice would be to use certified and reliable Security Monitoring solutions.
Once vulnerabilities are identified, an attack is usually simulated to test the effectiveness of security countermeasures.
The Risk Analysis
Risk Analysis, on the other hand, is a process of assessing the risks associated with the use of an information system or technology, helping companies develop risk management plans to mitigate or eliminate related hazards.
 The goal of Risk Analysis is to identify potential risks associated with the use of an information system and to assess the impact these risks could have on the company or organization.
The goal of Risk Analysis is to identify potential risks associated with the use of an information system and to assess the impact these risks could have on the company or organization.
Risk analysis relies on a variety of risk assessment techniques, such as assessment matrices, to identify potential risks associated with the use of a technology basing on the probability of occurrence and the impact these risks could have on the business or organization.
VAPT: Penetration Testing
Penetration tests are a fundamental cybersecurity tool and consist of a simulation of cyber attacks against an organization’s systems in order to identify and assess the vulnerabilities of those systems.
What is a penetration test?
A penetration test, also called a “pen test” or “ethical hacking,” is a simulation of a cyber attack by a team of cybersecurity experts to identify and assess vulnerabilities in an organization’s systems.
Penetration tests can be performed on any type of computer system, including web applications, networks, servers, mobile devices, desktop computers and other devices.
They are often conducted by computer security experts outside the organization, known as “penetration testers” or “ethical hackers,” who use the same tools and techniques used by malicious hackers.
Types of penetration tests
There are different types of penetration testing, each focusing on a different aspect of cybersecurity.
- Black box testing: the penetration tester does not have access to information about the system being tested, such as source code, login credentials, or network structure. This type of testing simulates an external attack by an unauthorized hacker.
- White box testing: the penetration tester has complete access to information about the system to be tested, including source code, login credentials, and network structure. This type of testing simulates an attack by a malicious insider with privileged access.
- Grey box testing: the penetration tester has partial access to information about the system to be tested, such as access credentials but not source code. This type of testing simulates an attack by an insider with restricted access.
VAPT: Vulnerability Assessment
Vulnerability assessment is a technique used to identify vulnerabilities in computer systems and assess the risk of a possible attack by hackers or other malicious actors.
What is vulnerability assessment?
Vulnerability assessment is the systematic analysis of applications, systems, and networks to identify any vulnerabilities that could be used by hackers or other malicious parties to gain access to or compromise a system.
The vulnerability assessment process uses a variety of techniques and tools, including port scanning, web application vulnerability testing, and mobile device scanning, in order to identify possible vulnerabilities.
Importance of vulnerability assessment
Vulnerability assessment is a key cybersecurity activity, as it helps identify vulnerabilities in systems and assess the risk of attacks by hackers or other malicious actors.
It also enables organizations to take a proactive approach to cybersecurity, preventing attacks before they occur.
Cyber Risk Management: Telsy’s proposal
To face the complications and risks derived from malicious actors or software vulnerabilities, Telsy offers a coaching and support service to companies aimed at assessing the degree of risk exposure of information and technology assets, also implementing sustainable and effective remediation plans.
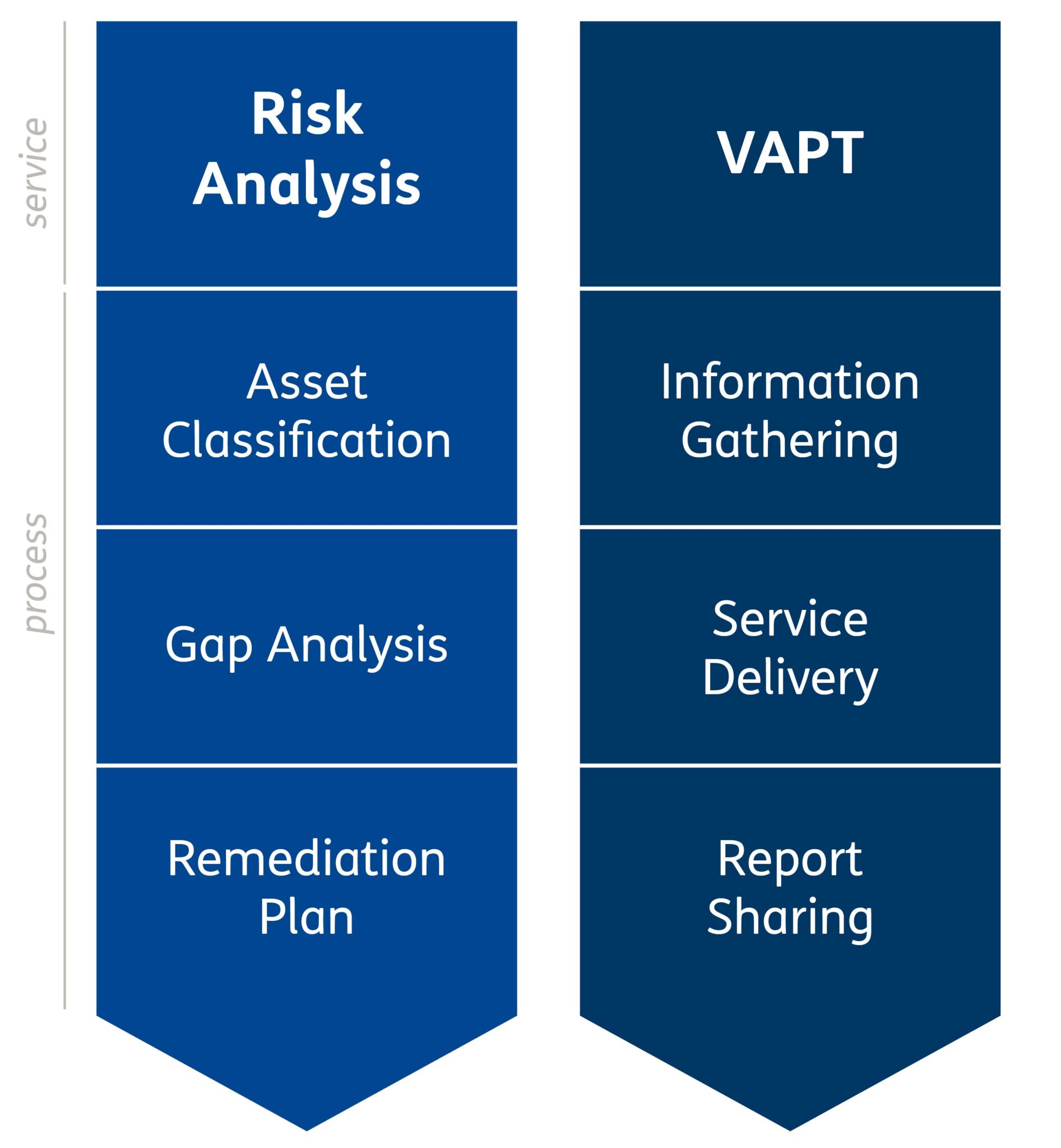
The service includes two macro-areas:
Risk Analysis
The Risk Analysis process is based on the adoption of sector standards and best practices and allows for the definition, implementation, and maintenance of a risk management model integrated into company processes, guaranteeing the homogeneity, consistency, and repeatability of the results achieved.
VAPT
The VAPT activities are carried out following the best practices of the sector through mixed techniques, combining automatic tools with manual activities to verify the security status of the systems and detect any vulnerabilities and their consequent exploitation.
Discover all Telsy solutions for Risk Management services and other preventive and reactive security tools dedicated to companies.
