Cyber Threat Intelligence: knowing and anticipating threats

Success in the digital age depends on the ability to validate complex information and leverage it to lead change.
For organizations, it is today necessary to equip themselves with tools that can enhance internal and external data, so that they can be made available to decision-makers.
What is Cyber Threat Intelligence?
According to Gartner’s definition, Cyber Threat Intelligence (CTI) is evidence-based knowledge about an existing or emerging threat, or danger to assets.
This intelligence can be used to corroborate decisions regarding response and/or prevention against the related threat or risk.
CTI can be understood as the knowledge to prevent and mitigate cyber threats in order to improve the security posture of organizations by enabling appropriate defense strategies.
Telsy’s Cyber Threat Intelligence
Telsy, the TIM Group‘s cybersecurity and cryptography competence center operating in TIM Enterprise, through its iSOC (Intelligence Security Operation Center) and experts offers a Cyber Threat Intelligence Suite equipped with dedicated professionals and proprietary technologies developed in-house.
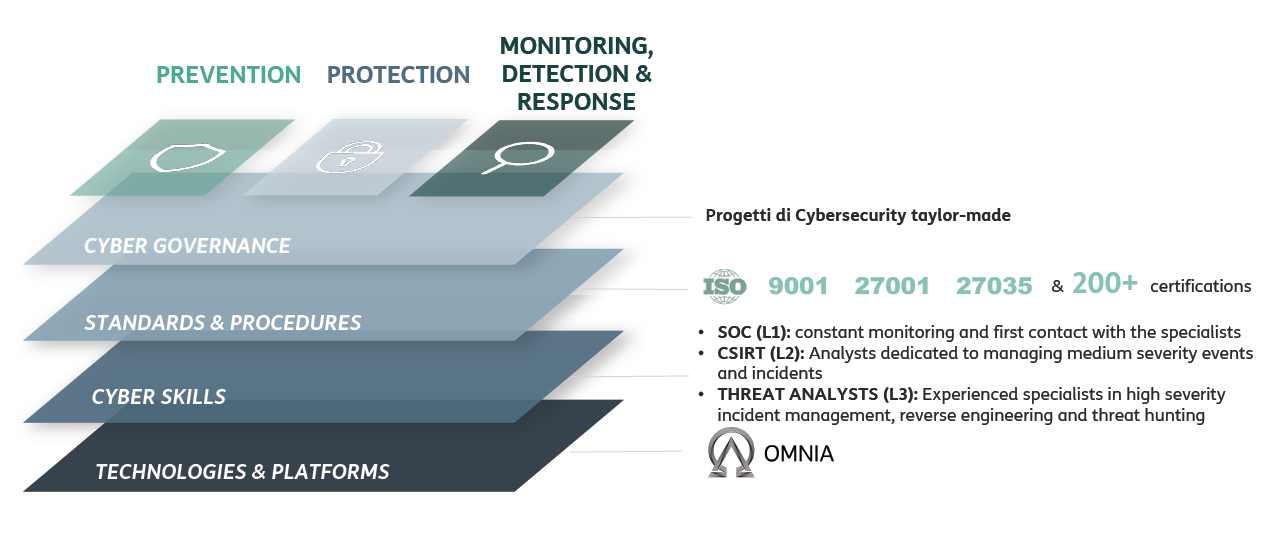
The Suite consists of four modules including technologies and operational capabilities in event analysis and management:
- Company Threat Intelligence
- Early Warning
- Threat Investigation
- Treat Intelligence Feed & Platform
Company Threat Intelligence
The Company Threat Intelligence Service provides comprehensive domain monitoring to protect organizations from vulnerabilities and/or data lakes.
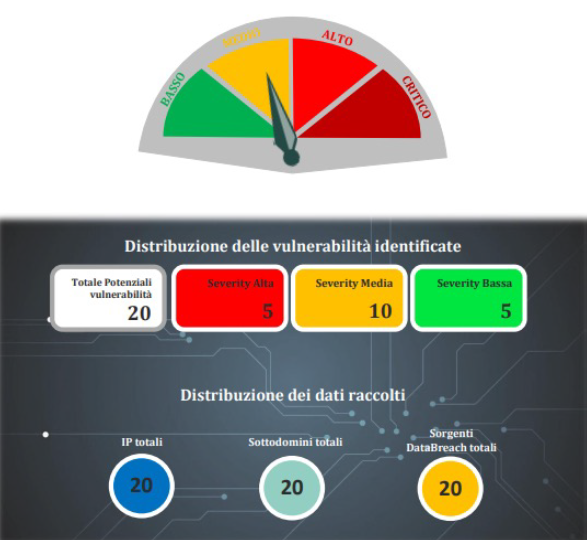 It is aimed at identifying any information available at both OSINT (Open Source Intelligence, publicly accessible) and CLOSINT (Close Source Intelligence, accessible on subscription or derived from confidential knowledge bases) levels.
It is aimed at identifying any information available at both OSINT (Open Source Intelligence, publicly accessible) and CLOSINT (Close Source Intelligence, accessible on subscription or derived from confidential knowledge bases) levels.
Threat Intelligence Gathering is carried out through a process of searching, identifying, selecting, and collecting information available both publicly and on dark web/deep web.
Then dedicated cyber defense analysts prepare a report that provides insight into criticality and data breach risk exposures on company domains.
The Company Threat Intelligence process is delivered through 5 phases:
- Setup – Mapping assets associated with the domain (subdomains, IPs, compromised emails, vulnerabilities on exposed services and applications);
- Research & Data Enrichment – Research conducted on OSINT and CLOSINT sources to identify compromised confidential information;
- Data Analysis – Observation conducted automated tools and analyst ratings (Severity and Confidence Rating);
- Reporting – Creation of a report providing the evidence obtained from the analysis;
- Cyber Specialist Feed & Support – The customer can request a meeting with Telsy’s cyber specialists to go over all the issues in the report.
Early Warning
The service allows the customer to reduce cyber risk exposure with timely reports on software and/or hardware vulnerabilities related to technologies in the customer’s perimeter.
Weekly reports, typically in advance of vendor communications, reduce the time to analyze, detect and extinguish vulnerabilities.
Service Delivery Phases:
- Setup – Creation of the customer’s list of technologies;
- Analysis – Matching between technologies and public databases (OSINT);
- Reporting – Timely notifications, weekly reports, and executive summary detailing vulnerabilities found, potential impacts, and suggestions on actions to be implemented.
Threat Investigation
Threat Investigation is a defensive activity that allows to detect and isolate those so-called “advanced threats” (as they are new and unknown) that escape detection by traditional security solutions, allowing to respond and anticipate the actions of cyber criminals or insiders.
Telsy’s Threat Investigation service consists of a specialized activity aimed at gathering evidence traceable to a specific anomaly or artifact encountered by the customer, with the goal of restoring business continuity through validation, understanding and reacting to events so as to prevent or mitigate their impact.
Again, service delivery follows a process consisting of:
- Customer manifestation of problems, anomalies or artifacts on their systems;
- Investigation combining automated analysis and expert insights;
- Technical report with event description, data enrichment, indicators of compromise (IoC) and attack mode (Kill Chain);
- Defense strategy planning and assurance to support business continuity recovery.
Threat Intelligence Feed & Platform
A module of Telsy’s CTI Suite that consists of two interoperating elements:
Feed
Provides incident responders with an information feed on methodologies adopted and attacks brought by threat actors with high technical expertise.
The service consists of a global information gathering and validation activity regarding threats, targets under attack or incidents that have occurred.
It provides the production and delivery of feeds/streams of information to be uploaded to the SIEM or Threat Intelligence platforms.
Platform
An interactive dashboard populated by feeds coming from the Threat Intelligence team detailing actors, threats, attack patterns, exfiltrated data and cyber incidents that have occurred.
The Threat Intelligence Feed & Platform service is divided into three distinct levels dedicated to specific types of stakeholders:
- Strategic – CISO, CIO, CTO and Executive Board
- Operational – Threat Hunter, SOC Analyst, Vulnerability Management, Incident Response
- Tactical – SOC Analyst, SIEM, Firewall, Endpoint, IDS/IPS
Learn more at www.telsy.com
