Unknown threat actor is using Agent Tesla variants against Oil&Gas and Energy Sector
On 02/07/2019, Telsy TRT catched a new malware variant belonging to Agent Tesla family addressed to companies operating in the Energy and Oil&Gas sector. Among these organizations, Telsy identifies a very large italian company with a strong international presence, especially in the UAE area.
Attack Vector
As in many cases we usually observe, the main attack vector used for spreading the malicious payload is email. In this case, we were able to collect some malicious messages sent by threat actor to different targets; these messages are oriented to spoof the identity of what we belive to be a real person involved in engineering field in UAE area. Indeed, we believe the threat actor likely performed an OSINT research before to start the campaign aimed at finding potential identities and useful arguments in order to maximize the probability of target infection.
Following the screenshot of the LinkedIn profile of the spoofed identity:
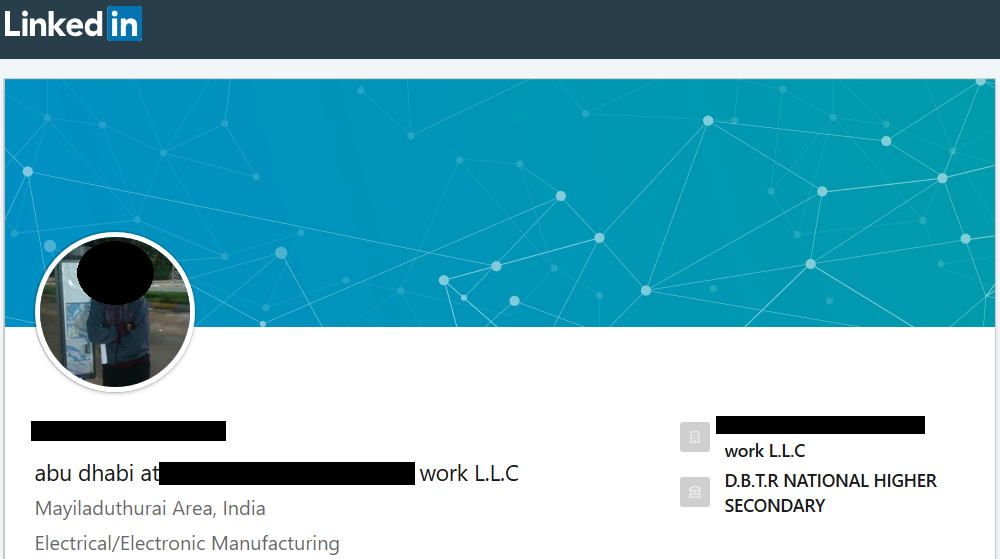
We performed some reverse research on images and information found over the linkedin profile concluding that it’s likely a licit one and has been used as useful identity for malicious communication.
Threat actor spoofed a convincing email source address simulating an official communication from the UAE branch of the impersonated organization. The real source of communication (IP address) is however a paid service (VPS) from M247 network, hosted in Romania.
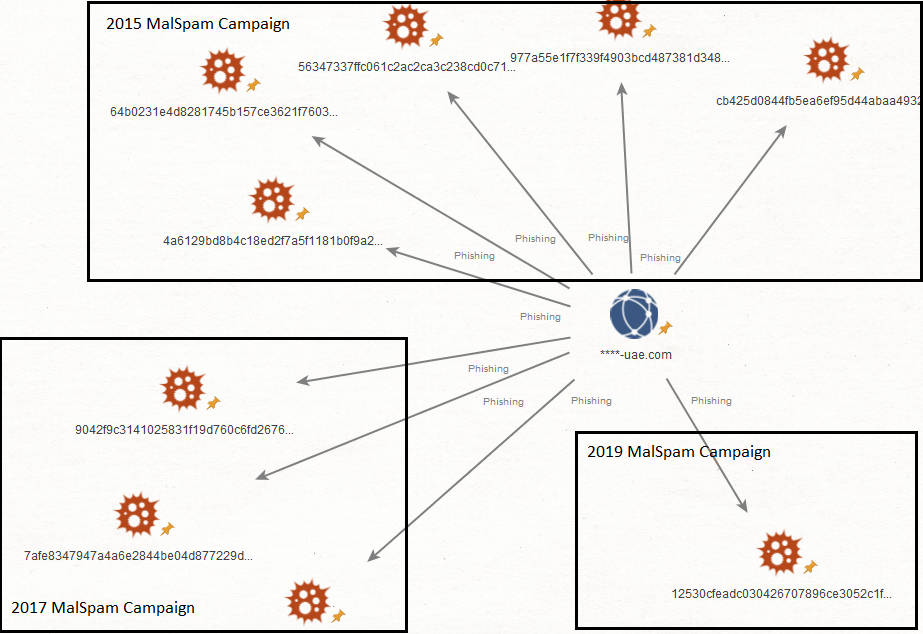
Quite interesting to note is that the spoofed email address is referencing a domain name that is not new in malspam history. We were able to track malware samples back to 2015, using similar techniques to deliver malicious payloads:
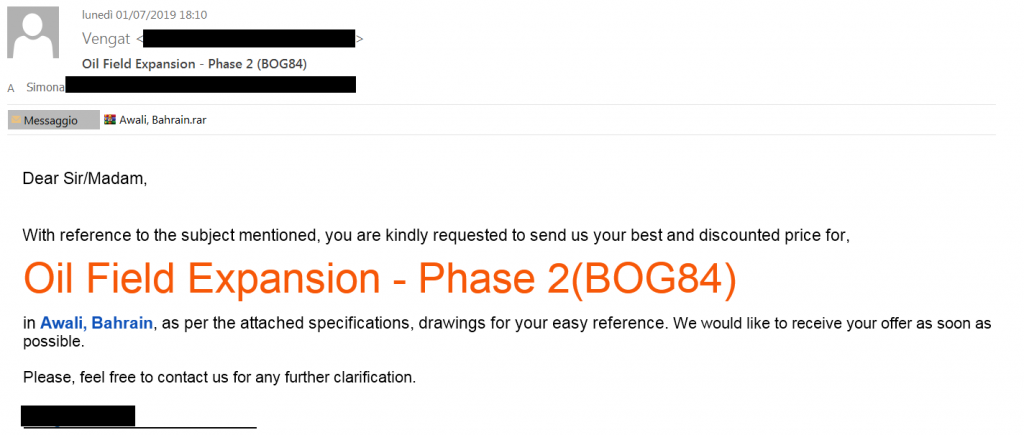
Following an example of the email message addressed to the italian company:
Payload
The delivered payload is a variant of Agent Tesla malware. Agent Tesla is .NET based keylogger and RAT available to many threat actors. It’s able to log keystrokes, take screeshots and beacon back login and passwords of the infected host. In this case, we observed a first stage malware (delivered attached to the email message into a .rar archive) written in MS Visual Basic language which represents a first level of execution in the cycle of installation and persistence of the malware.
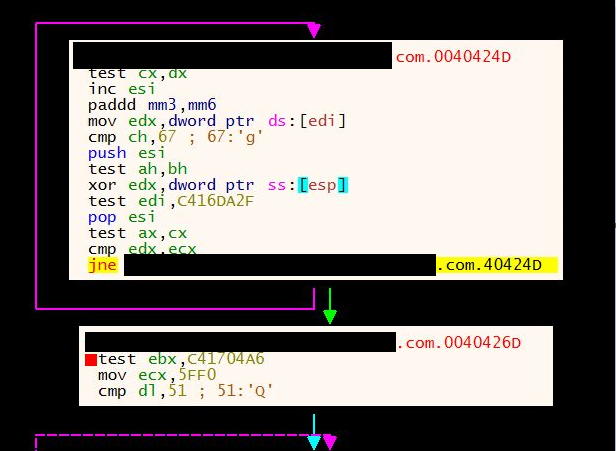
This piece of malware is going to unpack itself in order to spawn and execute a new PE within its memory region. Indeed it extracts a byte array from its resource and goes to overwrite the memory area of a child process previously created. Afterwards, it resumes the execution of the child process. In supporting these operations, the malware uses decoding cycles in order to recover instructions and structures, like the following frame of code extracted from one of the sample collected:
An interesting thing about the first stage payload is that it goes to retrieve a piece of scripting instructions quite different if compared to last versions of Agent Tesla packages we observed; here MOLLY and DAW take an essential role in choosing if run the primary malicious code and set persistency.
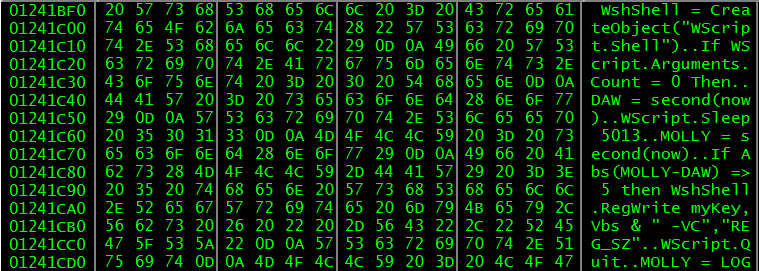
Beaconing
Malware is communication outside through SMTP protocol. It’s able to collect multiple information about the victim host such as, i.e.
- Computer Name
- OS
- CPU
- RAM
- IP
- Retrieved credentials from:
- Firefox
- Flock
- Chrome
- Thunderbird
- PostBox
- Outlook
Malware is able to take screeshots of the victim host and log keystrokes setting an hook through SetWindowsHookEx. Following a network dump of data sent to CnC while malware was dynamically analyzed:
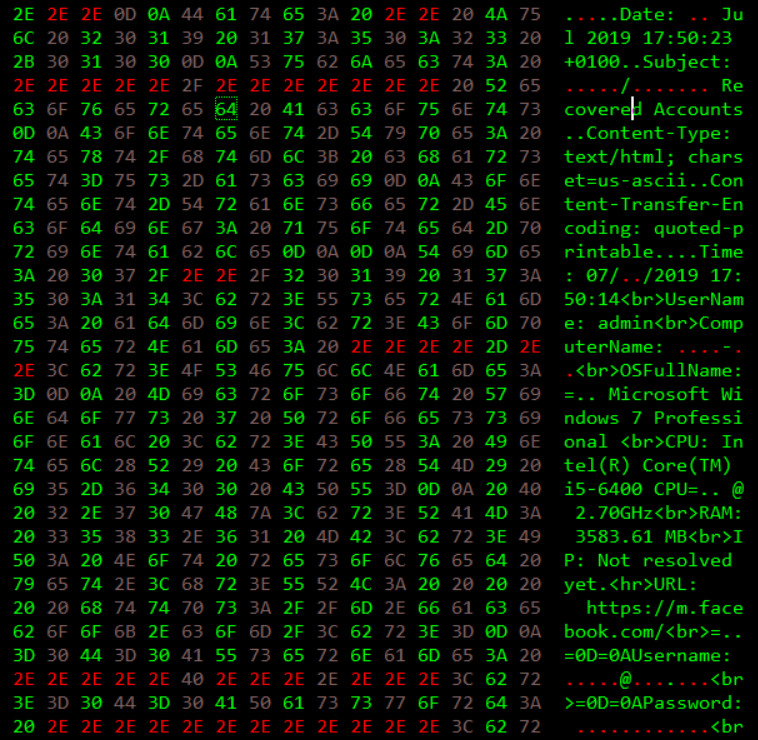
Telemetry
We are observing activities related to this threat in the countries shown below:
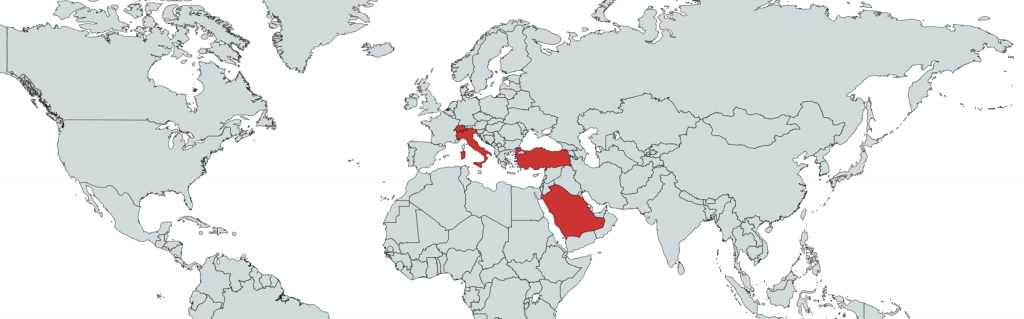
Mitigation
- Pay attention about any email attachments transmitted even from email addresses appearing known.
- Adopt a reliable EP protection software.
- Even in case of infection, it’s possible to avoid data exfiltration adopting a SecureDNS service. Telsy Free SecureDNS is currently blocking for free all communications directed to the full set of malicious domain names related to this campaign.
Conclusion
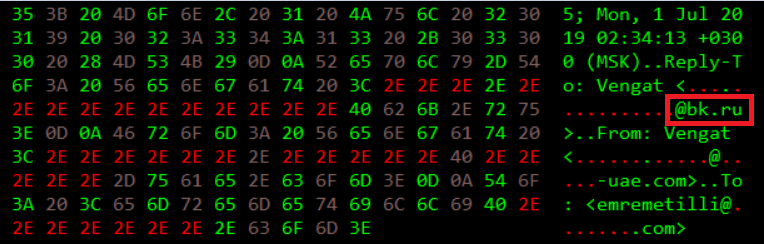
In relation to the type of attacks tracked so far, it’s possible to assess with a good degree of confidence that this campaign has been mainly aimed to hit a specific sector. Although it’s probably not a “state-sponsored” threat (currently it’s internally classified as a crime related threat by us) it is clear that, based on the functionality of the malware, the actor is clearly focused on specific information / data from energy and “oil & gas” sector. It’s interesting point out that we observed a reference to a bk.ru email address in the Reply-To field of the header of one malicious email message.
Finally, we would remember that such campaigns are not new to the italian security community. Recently, on 09/04/2019, the D3Lab researchers highlighted techniques and methods quite similar to this one.
We report their analysis below for further information:
IoC
MD5: F75AECDAF8A05D3E33438C7D3264404C
MD5: AA584184A3448C11A83C510E75572FC3
MD5: 2F204E854CD01CE431BB2A2A55C28445
FILE: “%temp%\subfolder\filename.vbs”
FILE: “%temp%\subfolder\filename.exe”
Further IoCs, Yara / Snort rules and a deeper report in PDF format are available by subscribing a Telsy TI service up to tlp:green.
For more related articles, check our blog.
