APT34: New leaked tool named Jason is available for the mass
In the afternoon of 03/06, Lab Dookhtegan released a new tool they report belonging to the hacking arsenal of the group APT34.
This hacking tool seems to be useful in order to hack email accounts and consequently exfiltrate data. The archive we got is composed by the following file
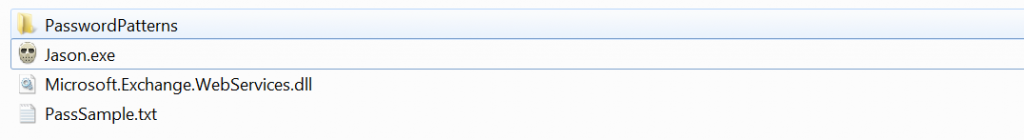
First analysis identified two executable files and some others in txt format likely used in supporting tasks.
The file Microsoft.Exchange.WebServices.dll is an official component of Microsoft Exchange communication suite.
We performed a quick AI powered malware scan getting no results over the first component extracted:
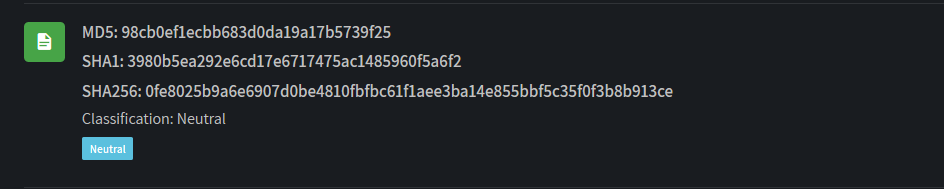
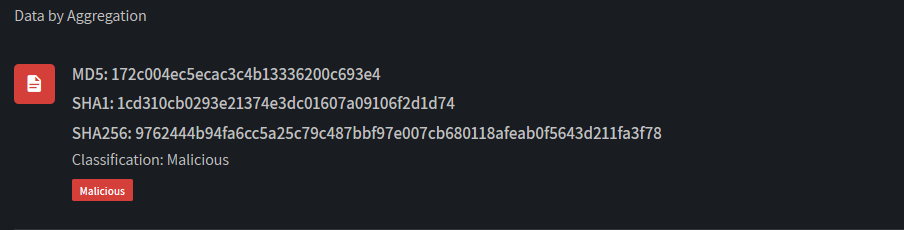
The file Jason.exe is a dot NET custom tool seems to be capable to perform hacking attempts against email accounts.
The results of the same AI powered scan against Jason.exe is reported following:
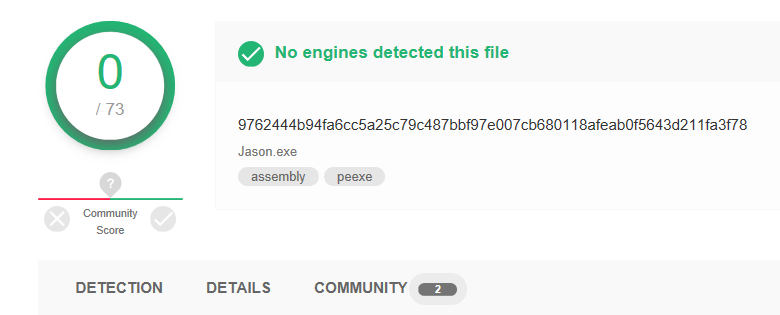
Instead, we noticed that no engines on VirusTotal recognized it as malicious at the time of analysis. We have to say, however, this is to be classified as an hacking tool and usually does not constitute, by itself, something that can directly compromise the security of the system where it is executed. After considering this, it’s good practice to classify these tools as potentially malicious by security vendors.
An image showing the VT scan results is reported:
Insights
The tool has an user interface quite intuitive and its purpose is easily deducible from the fields and functions it makes available
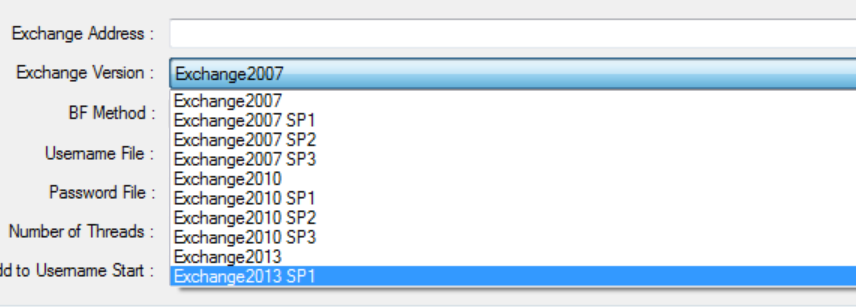
This is to try to hack exchange email accounts by brute forcing authentication credentials against email servers. The tools supports OAB and EWS brute forcing methods and it’s designed to collect user/pass lists directly from input text files.
It supports multi threading execution. The numbers of threads to be used is choosen by operator at the time of scan configuration:
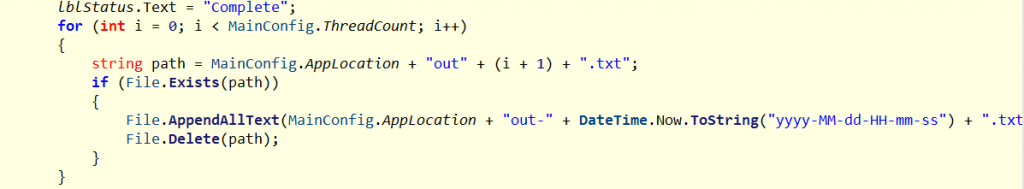
The results of scan is saved into another .txt file named out-[datetime].txt
while information about running activities and debugging is saved into log.txt file
Conclusion
Lab Dookhtegan continues to leak potential APT34 tools and identities. This tool is a simple old-style appearing but potentially very effective one. For what we can suppose it could have been in use for a long time in the group’s arsenal and seems that many versions have been released over the time. In this case this specific version [7.0] may have been released in the first days of 2019.
Update 04/06/2019
We publicly released our tlp:white YARA detection rule to hunt malware samples belonging to this HKTL family. It’s available on our GitHub dedicated repo.
