ICT Risk Management: how to set up your cyber defenses
 IT security is a complex and evolving field and needs a systemic approach to managing cyber incidents.
IT security is a complex and evolving field and needs a systemic approach to managing cyber incidents.
These incidents do not always concern malicious attacks, but can be the result of ill-conceived or incorrectly carried out practices, weak defense strategies, failure to comply with the current regulatory framework, or all those factors that in any case fall in a single conclusion: economic losses (and not only) for the companies that are affected.
Reactive and proactive ICT Risk Management
The whole sector now agrees on the evolution of the IT risk approach model.
There is therefore the need to move from a reactive to a proactive approach. In this case, we are speaking about organizational procedures, rather than technical ones.
We move from a prevention model plan, usually developed on the basis of immediate business needs, to one which analyzes the context within which the company operates, evaluates the prospects to get the medium and long-term needs, and finally models a complete risk management plan.
Furthermore, in a such dynamic and uncertain context, constant information monitoring through a threat intelligence activity, becomes particularly important.
Cyber risk and its characteristics
 Cyber risk has some peculiarities that differentiate it from the typical risks associated with computer security.
Cyber risk has some peculiarities that differentiate it from the typical risks associated with computer security.
Traditionally, risk assessment is based on a correlation between threats and vulnerabilities that lead analysts to identify, through qualitative or quantitative risk analysis methodologies, the probability and impact of an adverse event.
In the cyber risk case, the determination of these parameters is more difficult and nuanced.
Alongside the traditional risk scenarios and the related countermeasures (malware, man-in-the-middle, phishing, distributed denial-of-service, cross-site scripting, password cracking…) we find ourselves, for example, having to face a series of unknown vulnerabilities (so-called zero-day) and therefore unpredictable, which can be exploited by attackers and for which a proper reaction capacity is required, also for the normal operations possible restoration.
The importance of Risk Management
According to the Clusit 2022 report, last year 78% of total attacks had critical and high impact, up from 2020/2021 when they were 50%, and only 0.6% of these had a low impact. This shows that the attacks are not only growing in quantity, but also in quality.
This scenario, together with poor cyber risk awareness and a low knowledge level of the most suitable mitigation tools, can lead to real disasters for a company and for the institutions or connected infrastructures (especially if critical).
Making your staff aware of the IT risks to which they are exposed and the possible repercussions consequences on the company business is undoubtedly one of the main steps in building an effective cyber defense strategy. But security awareness alone is not enough.
In fact, it is necessary to build a reliable ICT risk management plan, which includes targeted investments in cybersecurity and periodic IT infrastructures and systems vulnerabilities and tightness checks, in order to guarantee business continuity even in the presence of security incidents.
ICT Risk Management: Telsy’s proposal
For any organization, understanding its own current security posture state requires a constant risk assessment to which it is exposed, security standards, and cybersecurity regulations.
To meet these needs, Telsy offers a coaching and support service to companies aimed at assessing the exposure degree to information and technological assets risk and at implementing sustainable and effective remediation plans.
The service includes two macro-areas:
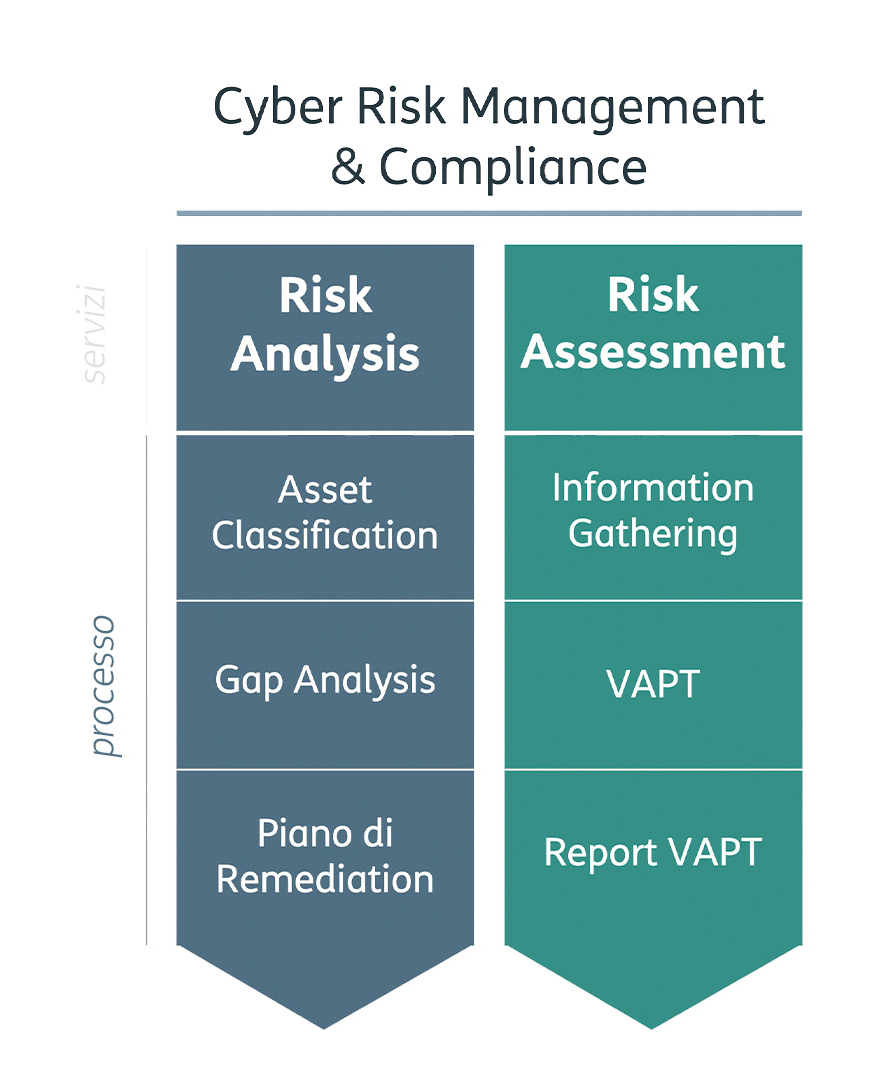 Risk Analysis
Risk Analysis
The Risk Analysis process is based on the adoption of sector standards and best practices and allows for the definition, implementation, and maintenance of a risk management model integrated into company processes, guaranteeing the homogeneity, consistency, and repeatability of the results achieved.
The process is delivered in three steps:
- Asset Classification
- Gap Analysis
- Remediation plan
Risk Assessment
The Risk Assessment activities are carried out following the best practices of the sector through mixed techniques, combining the use of automatic tools with manual activities in order to verify the security status of the systems, and detect any vulnerabilities and their consequent exploitation.
The process is delivered in three steps:
- Information Gathering
- VAPT (Vulnerability Assessment and Penetration Test)
- VAPT reports
Discover all Telsy solutions for Risk Management services and other preventive and reactive security tools dedicated to companies.
