Protect smartphones and tablets from cyber risks: the mobile security

Smartphones, tablets, smartwatches, and in general all so-called “smart” devices, are today indispensable tools for companies, public administration, and private citizens.The mobility and immense technological capabilities of these devices actually broaden the perimeter to be defended and the risks to be prevented to avert damage.
Careless or unsafe use of these mobile devices can lead to serious consequences, from espionage to the compromise of data or production processes, also putting our physical safety at risk in case of personal data theft.
Along with proper security awareness about the informed use of our smart devices, it is necessary to get tools and technologies that help us to keep in check the countless risks that are always just around the corner.
Threats to mobile devices and mobile security
Our smartphones contain valuable information for cybercriminals, who target them with increasingly new and sophisticated techniques.
Malware, spyware, fake antivirus, open Wi-Fi networks, and social networks, the dangers are everywhere.
Thus, there comes the need to resort to techniques, solutions, and technologies that enable people to defend their mobile devices from today’s dangers. In this sense, we are talking about “mobile security.”
Mobile security refers to the strategy, infrastructure, and software used to protect users’ mobile devices, including smartphones, tablets, and laptops.
Cybersecurity applied to mobile devices (mobile security) involves protecting data on local devices, connected devices, and network tools.
As mobile devices are increasingly used by users for their convenience, compared to desktop systems, they are unfortunately also favorite targets for cybercriminals.
The main threats to mobile devices
The operating systems of smartphones and smart devices (for convenience we will refer to smartphones) have a different architecture from computers, and therefore the attack techniques are also different. Both Android and iOS, for example, are operating systems where applications operate without having complete access to the system.

In smartphones, applications are segregated in a sandbox and have access only to those parts of the operating system to which we give access permissions.
Today, the most exploited method for malware to infiltrate a mobile device is through the download of a malicious app. Cybercriminals build apps containing hidden malicious functionality to evade detection by the control processes of the stores from which the apps are downloaded.
The major (and most frequent) threats to mobile devices are basically as follows:
- Malicious applications
- Vulnerabilities in operating systems
- Smishing (SMS phishing)
- Spyware
Unlike with computers, ransomware, which encrypts files has not been very successful in the mobile world. This is because smartphones back up to the cloud. So if users back up regularly, there will be no need to pay a ransom to get their files back, and it will be enough to retrieve them from the backup. Therefore, cybercriminals have not found this type of attack convenient to date.
Good rules for prevention
People and companies tend to underestimate the risks of “smart” mobile devices, even because they are devices with which we are very familiar in their use.
Instead, this familiarity and the constant browsing of our smartphones, even while we are doing other things, exposes us to risks of all kinds.
So let’s summarize some of the good rules to defend against mobile malware:
 Install apps only from reputable sources, avoiding those of dubious reputation and checking user feedback and reviews;
Install apps only from reputable sources, avoiding those of dubious reputation and checking user feedback and reviews;- Verify which of our personal data is processed by the app;
- Do not enable the option to install apps from unofficial stores;
- Granting the app only the permissions really needed to function;
- Do not trust emails or text messages advising us to install an app;
- Do not click on links or attachments in emails or text messages, and avoid suspicious URLs from unknown origin;
- Always log out of applications;
- Always keep the operating system (and also applications) up-to-date;
- Never provide personal information and credentials via email or text messages;
- Do not use public Wi-Fi connections to conduct transactions or exchange confidential data;
- Back up device data regularly;
- Set a password lock on the device;
- Especially for businesses, install Mobile Device Management (MDM) systems.
This non-exhaustive list collects the generally most effective best practices for protecting our devices and preserving the security of the data and information they contain.
However, these actions alone can be insufficient, especially if we are talking about companies and organizations, at various levels. Therefore, it is necessary to have specific security solutions tailored to the specific need.
To meet this need and defend users (companies, PAs, and individuals), Telsy presents a portfolio of solutions dedicated to mobile security.
TelsySpywareDetector
As a support against the dangers exposed by spyware and similar threats, Telsy presents TelsySpywareDetectorDevice, a solution designed to detect the possible presence of spyware in mobile devices (currently available for iOS; Android version in development), without compromising user privacy.
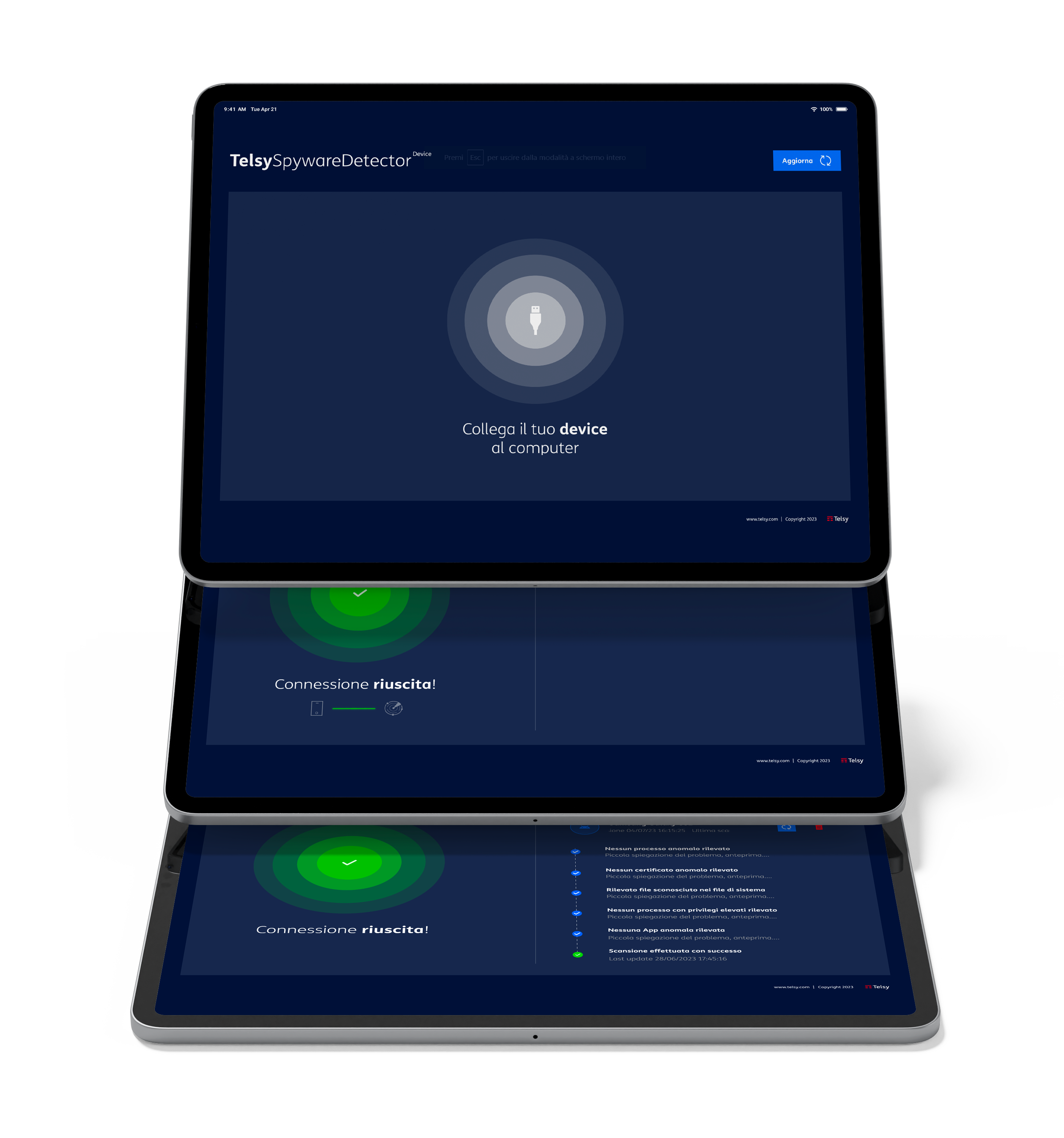 The system does not take any data on the device, ensuring user privacy.
The system does not take any data on the device, ensuring user privacy.
The software, installed on Android tablets, allows in-depth and automated forensic analysis of all processes, executions, and file ownership on the mobile device, connected via USB cable.
At the end of the analysis, a detailed report of any anomalies detected is generated, which can be viewed and downloaded from a dedicated web dashboard.
The user will be able to view, print, and/or receive via e-mail the full report with the details of the scan like device info, unknown files in system paths, processes with elevated privileges, installed apps, apps with anomalous certificates, and anomalous processes.
Find out more about TelsySpywareDetector by writing to contact@telsy.it.
TelsyMobileDefender
TelsyMobileDefender is an innovative and complete cloud solution that provides all the tools needed to manage, monitor, and protect Android and iOS devices from data theft and cyber intrusions.
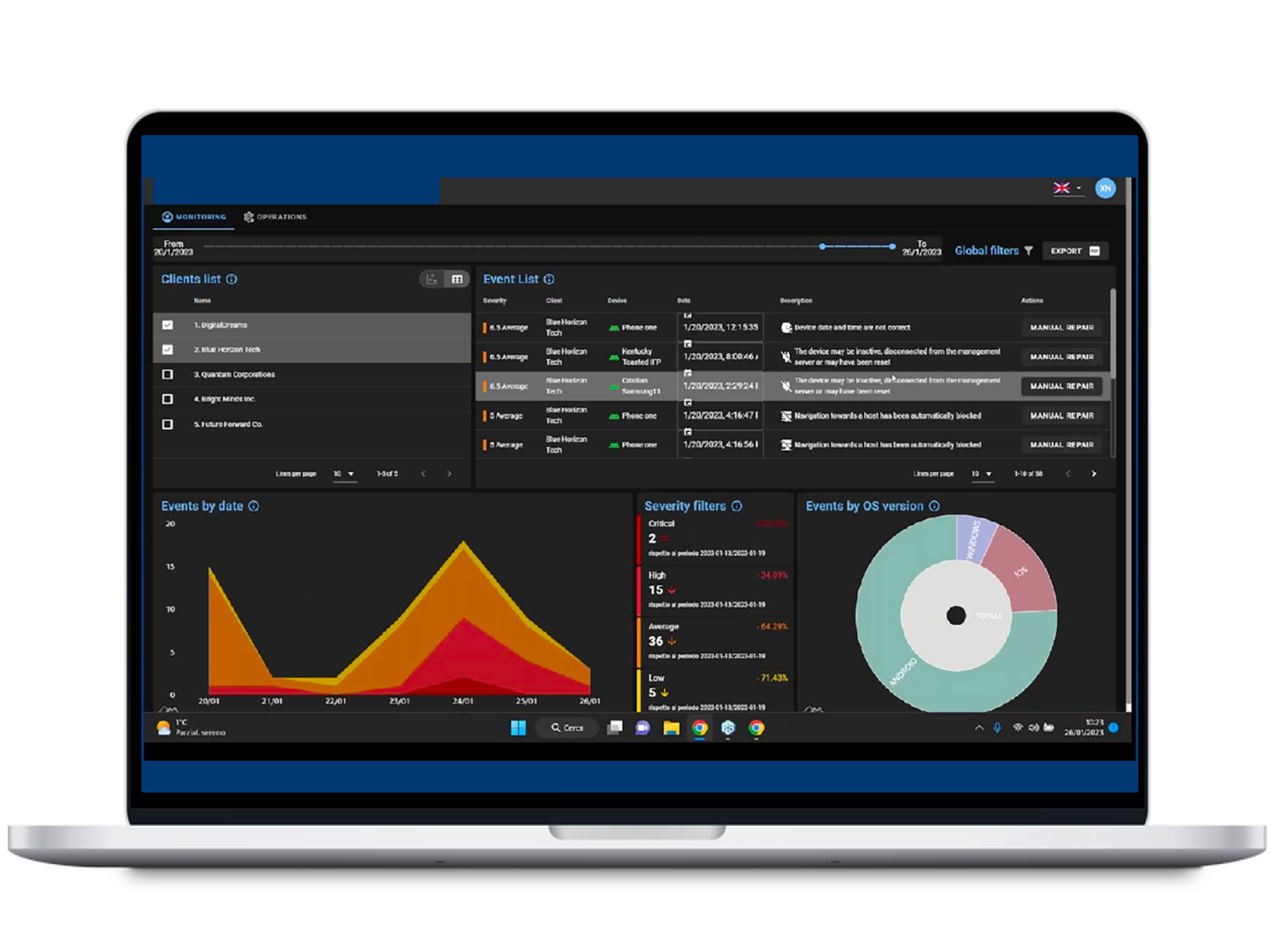 In it, an Endpoint Management system and a Threat Defense module (MTD) integrated with Telsy’s SIEM and SOC coexist, providing 3 lines of defense.
In it, an Endpoint Management system and a Threat Defense module (MTD) integrated with Telsy’s SIEM and SOC coexist, providing 3 lines of defense.
Through an agent installed on the devices, it is possible to uniformly manage Apps, APKs, file resources, certificates, notifications, settings, and updates from a single administration panel, ensuring smooth and optimal operation across the entire fleet.
The platform also makes it possible to monitor all events that could lead to possible system security issues, breaking them down by criticality.
Learn more about Telsy’s cyber solutions and other Managed Security Services (MSS) dedicated to mobile security.
