Threat Hunters vs Red Teamers. A meeting in the cyber space…
Recently, a new wave of malicious decoy Microsoft Office documents addressed exclusively to a central country of the european geographical area was intercepted by Telsy TRT. These have been collected while landing on a media sector company. Observed TTPs did not lead to any known threat actor and initially we were imagining that a new group was coming out of the shadow…
Who was operating behind this campaign seemed to use different infection methods to reach the execution of its 1st stage payload, including the adoption of the “EvilClippy” tool, released during a BlackHat Asia talk (March 28, 2019).
However, after some time, we gathered evidence that led us to believe that this operation was a sort of “APT” exercise or attack simulation performed by a company focused on offensive security field.
After a necessary exchange of messages this assumption was confirmed and we decided to write this article mainly for two reasons:
- An unexpected meeting between two work groups actively involved in the cyber defence arena on different sides of the barricade is quite unusual in the cyber space.
- Although we are not going to reveal the adopted techniques or too much details about used tools, we want to pay something to this “red team” for interesting techniques put in place.
What is “EvilClippy”
According to its own description, EvilClippy is “A cross-platform assistant for creating malicious MS Office documents. Can hide VBA macros, stomp VBA code (via P-Code) and confuse macro analysis tools.”
Its major features are:
- Hide VBA macros from the GUI editor
- VBA stomping (P-code abuse)
- Fool analyst tools
- Serve VBA stomped templates via HTTP
- Set/Remove VBA Project Locked/Unviewable Protection
Always referring to its own description “this tool is capable of getting a default Cobalt Strike macro to bypass all major antivirus products and most maldoc analysis tools (by using VBA stomping in combination with random module names.”
An multi-engine scan result for one of the malicious document collected by us seems to confirm the effectiveness of this tool in evading common security solutions and in confusing static analysis activities.
1st stage payload
The malicious documents collected, as mentioned, present different types of combinations useful for the purpose of carrying out the infection of the victim systems.
Over the already quoted EvilClippy tool, we have detected the use of macro code in conjunction with powershell launched through Schedule.Service Objects.
The part of malicious code referred by this macro is a fairly simple but still effective fragment of a powershell code. It s enough to guarantee the closing of the first step of infection.
2nd stage payload
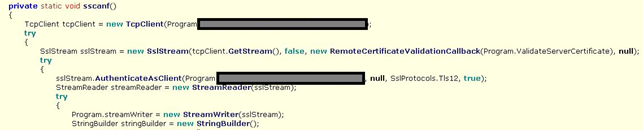
The second stage payload is an highly obfuscated .NET reverse shell. Once downloaded it’s launched by the PS code above and then runs “cmd.exe” establishing a remote connection with its CnC by copying the resulting command buffer into the communication channel, allowing the remote attacker to take the control of the victim system.
Here some snapshots of what observed while reversing this piece of malware:

This is the same code in a more readable form:
Conclusion
Unexpectedly meet red teamers actively engaged in offensive security phases is not a so common thing. We really had too much fun in tracking these guys during their “authorized access attempts”. For once, it was a pleasant to have the surprise of discovering “colleagues” operating like a real threat actor in the field. Good hacking guys!
Check other cyber reports on our site.
