Secure collaboration

In the office, on the road, at home, and in many other places, we often use tools and devices constantly connected to the Internet.
This condition has greatly increased the attention, not particularly felt until a few years ago, to privacy and personal or sensitive/confidential data security issues, especially if related to one’s profession.
Whether it is messages exchanged with classic instant messaging apps, work videocalls, or in-person meetings, protecting one’s conversations and maintaining a sufficient degree of confidentiality is essential if one does not want to incur theft of intellectual property or personal data.
Telsy’s secure collaboration offering
Telsy’s secure collaboration portfolio includes many products and services dedicated to securing our communications and remote collaboration, such as video conferencing tools, ultrasonic jammers, messaging apps, and ultra-secure smartphones.
Let’s look at them in more detail.
TelsyInTouch: collaborate and interact securely
The growing use of phones and instant messaging apps for business purposes, along with the consequent increase in risks related to the security of communications passing through them, highlights the need for tools that ensure the confidentiality of the exchanged contents.
 TelsyInTouch is an integrated solution (App + Smartphone) created to provide companies and government agencies with a robust and secure device to conduct sensitive communications in all operational environments.
TelsyInTouch is an integrated solution (App + Smartphone) created to provide companies and government agencies with a robust and secure device to conduct sensitive communications in all operational environments.
The solution consists of two integrated and complementary elements that together provide the necessary cyber and cryptographic security:
TelsyInTouchPhone
TelsyInTouchPhone are next-generation smartphones configured at the kernel level, Common Criteria 3.1 and 3.2 certified for maximum COMSEC and CIS security.
Appropriately developed to minimize the attack surface, they provide only the functionalities that reflect the requirements defined by the specific customer.
The solution is available in both iPhone and Google Pixel 6 versions.
TelsyInTouchApp
A secure collaboration app developed by Telsy to ensure the protection of users’ data and conversations through sophisticated security layers, such as specific NIST- and FIPS-certified encryption protocols and the proprietary TelsyGuard VPN.
The user experience of TelsyInTouchApp is similar to the most popular messaging apps on the market and allows text messaging, audio messaging, calls, video calls, and file transmission in total security.
How to protect your meetings with TelsyATMO
During a business meeting, we are often exposed to the risk of eavesdropping aimed at espionage or information theft.
Thus, mobile digital devices such as smartphones, tablets, and smartwatches are dangerous vulnerability vectors.
These, due to the inability to know if and when hostile software is using the microphone, offer dangerous opportunities for malicious attackers.
The TelsyATMO system was born from the need to protect sensitive or confidential information and communications against risks of eavesdropping.
 Apparently, a hi-tech glovebox, TelsyATMO is an ultrasonic audio jammer that inhibits malicious applications on compromised smartphones from listening to ongoing voice conversations.
Apparently, a hi-tech glovebox, TelsyATMO is an ultrasonic audio jammer that inhibits malicious applications on compromised smartphones from listening to ongoing voice conversations.
With this capability, the system prevents any conversation held in the presence of mobile devices from being intercepted.
Whether it is a table with people talking or a video conference, TelsyATMO provides an efficient sonic shield that can disturb any incoming sound waves to a device, preventing any unwanted apps or malware from recording sounds or conversations.
TelsyATMO specifications
TelsyATMO consists of an open casing in which one or more mobile devices, such as smartphones or smartwatches, can be stored, ensuring they remain visible, accessible, and reachable due to its transparent design.
This allows for at-a-glance evidence of any notifications, communications, and system statuses at all times.
 Within the casing space, TelsyATMO emits ultrasonic jamming signals inaudible to the human ear.
Within the casing space, TelsyATMO emits ultrasonic jamming signals inaudible to the human ear.
Thanks to these ultrasounds, which saturate the microphones of the devices housed in it, a distortion of the input signals causes them to become unrecognizable to any listening object.
Those features ensure secrecy in confidential contexts.
TelsyATMO is equipped with a wireless battery charger for the devices housed in it, along with a dimmable diffused lighting system that can be controlled remotely, via a special remote control.
The sonic protection function and wireless charging for devices can also be turned off via a simple switch.
Secure video conferencing with TelsyAntares
The growing demand for videoconferencing solutions and the growth of attacks and fraud related to the content of the information exchanged, make clear the need for secure solutions that minimize risk.
TelsyAntares is a web conferencing platform developed by Telsy that uses asymmetric encryption protocols to secure participant authentications.
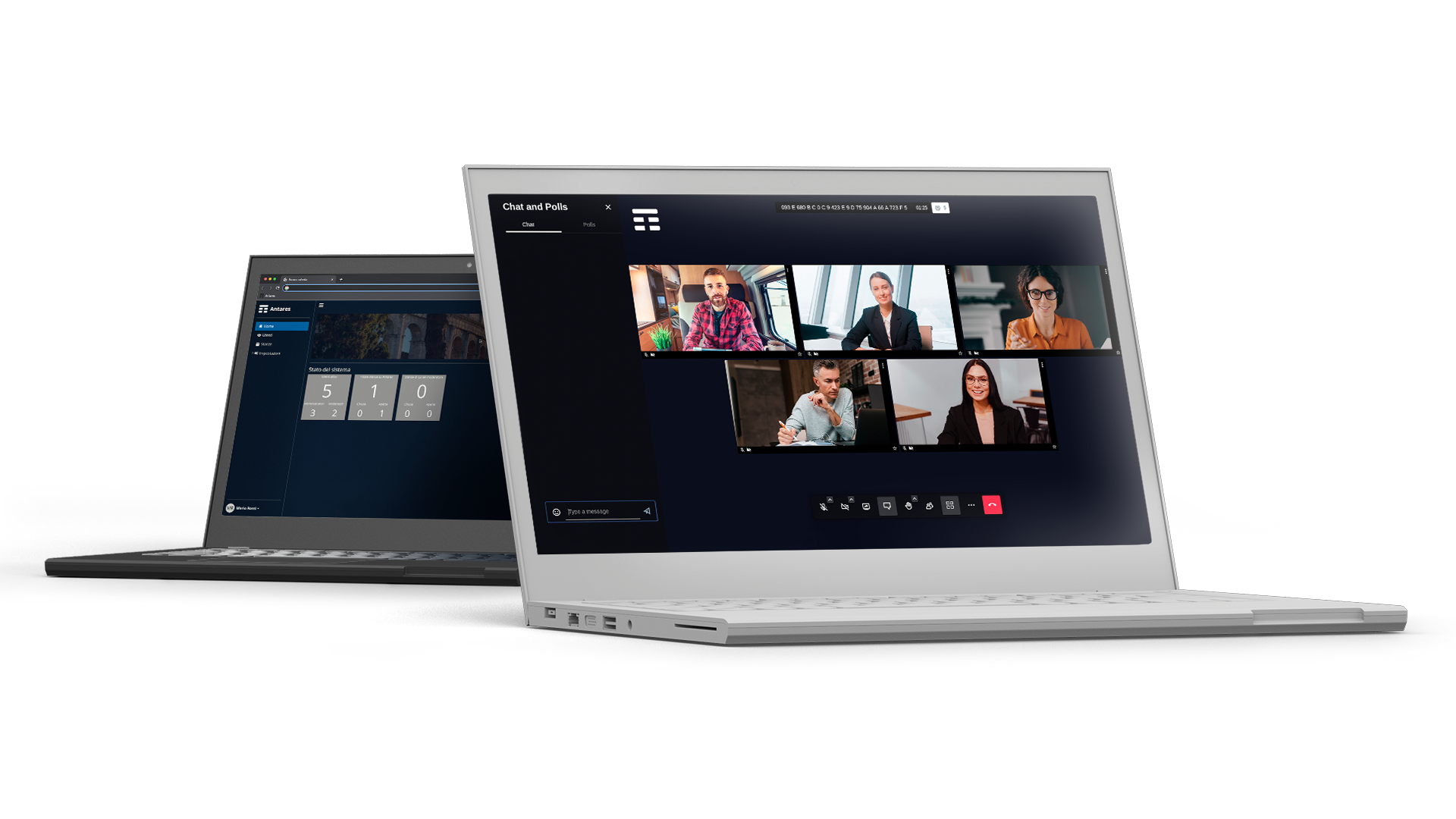 It is a solution developed to enable quick and easy configuration for any usage environment, providing higher levels of security than any other video conferencing solution. In fact, cryptographic keys are held and managed exclusively by the owner, without external mediation.
It is a solution developed to enable quick and easy configuration for any usage environment, providing higher levels of security than any other video conferencing solution. In fact, cryptographic keys are held and managed exclusively by the owner, without external mediation.
As an additional layer of security, TelsyAntares also allows the application of end-to-end encryption where cryptographic keys are available only to the participants of the current call, narrowing the surfaces of vulnerability against sniffing and similar attacks.
TelsyAntares encryption and security
The approach used in the development of TelsyAntares is Zero Trust. Therefore, all internal and external flows are encrypted.
Keys and passwords are loaded into the system and protected with elevated access privileges or stored on encrypted key-value databases.
Externally exposed TelsyAntares Rest APIs are authenticated with Bearer-type TelsyAntares JWT tokens, passed in the HTTP Authorization header, and sensitive public APIs are protected with API throttling mechanisms.
Telsy’s secure collaboration solutions
Telsy represents a national benchmark in communications security.
Thanks to more than 50 years of experience and tireless research, Telsy cryptographic systems guarantee the highest standards of security in data transfer and communications.
The integration between cryptographic solutions and cybersecurity services, paired by high-profile experts, makes Telsy’s offerings a pool of expertise capable of delivering cutting-edge proprietary products and technologies and developing systems that protect communications to meet evolving threats.
Learn more about these and Telsy’s other Crypto, Cyber, and Quantum solutions.
