The security of mobile devices: TelsyMobileDefender

Smartphones are today an indispensable tool for businesses, expanding the perimeter to be defended and the risks to be prevented to avoid harm.
Careless or unsafe use of mobile devices can lead to serious consequences, from espionage to compromising data or production processes.
Threats to mobile devices and mobile security
Our smartphones contain valuable information for cyber criminals, who target them with increasingly new and sophisticated techniques.
 Malware, spyware, fake antivirus, open Wi-Fi networks and social networks, the dangers are everywhere.
Malware, spyware, fake antivirus, open Wi-Fi networks and social networks, the dangers are everywhere.
Thus, there comes up the need to resort to techniques, solutions and technologies that enable people to defend their mobile devices from today’s dangers. In this sense, we are talking about “mobile security.”
Mobile security refers to the strategy, infrastructure, and software used to protect users’ mobile devices, including smartphones, tablets, and laptops.
Cybersecurity applied to mobile devices involves protecting data on local devices, connected devices, and network tools.
As mobile devices are increasingly used by users for their convenience, compared to desktop systems, they are unfortunately also favorite targets for cyber criminals.
To meet the users’ needs (businesses, PAs, and individuals), Telsy proposes a dedicated mobile security solution: TelsyMobileDefender.
TelsyMobileDefender
TelsyMobileDefender is an innovative and complete cloud solution that provides all the tools needed to manage, monitor and protect Android and iOS devices from data theft and cyber intrusions.
In it, an Endpoint Management system and a Threat Defense module (MTD) integrated with Telsy’s SIEM and SOC coexist, providing 3 lines of defense.
Through an agent installed on the devices, it is possible to uniformly manage Apps, APKs, file resources, certificates, notifications, settings, and updates from a single administration panel, ensuring smooth and optimal operation across the entire fleet.
The platform also makes it possible to monitor all events that could lead to possible system security issues, breaking them down by criticality.
TelsyMobileDefender: security features
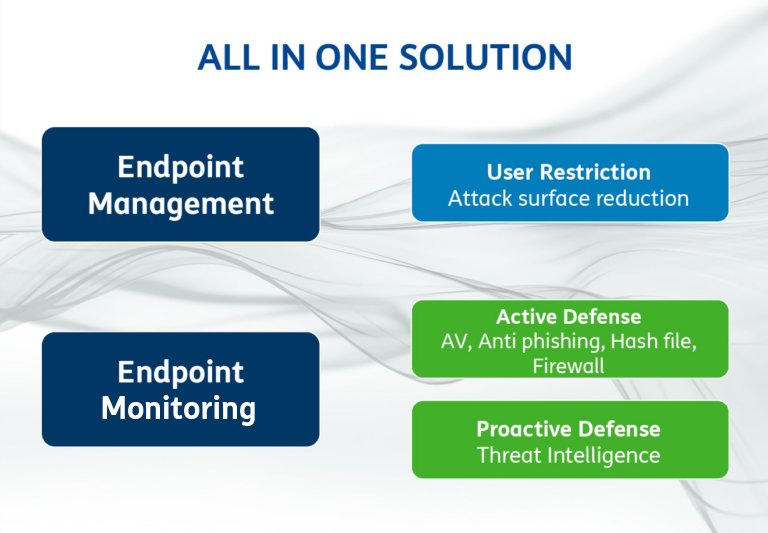 Here follows some of the main security features of TelsyMobileDefender:
Here follows some of the main security features of TelsyMobileDefender:
- DNS security: safe web browsing module that blocks potentially malicious sites;
- Advanced antivirus and anti-malware scanning: scanning for malware, Trojans and multi-sources ransomware;
- Anti Phishing: reliability check of URLs typed or sent via sms, email, messaging as potential attack vectors (pass steeling, phishing, etc.) and blocking the possible malicious ones;
- Smart Firewall: preconfigured firewall capable of blocking more advanced threats in the bud;
- Hash file check: reliability check of downloaded file (done manually, not present in continuous monitoring);
- TOR node check: ability to identify a potential IP address as a TOR exit node;
- OSINT check compromises capability: search for information of possible compromises from open sources on IPs, files, emails, names;
- Security pattern creation and management: customization, through the indicators of compromise (IoC) choice, and security patterns by single, group, or complete device.
Telsy’s Threat Intelligence
With the company’s Theat Intelligence capabilities (professionals, proprietary technologies, dedicated infrastructure), TelsyMobileDefender dialogues and interfaces with Telsy’s SIEM and SOC.
SIEM
Leveraging AI and correlation algorithms, TelsyMobileDefender can detect suspicious activity that may indicate credential compromise or internal threat by combining the various seemingly low-risk events.
SOC
Security experts constantly operating to ensure real-time threat detection and prevention and ensure that customer and user data protection is always optimal.
TelsyMobileDefender reporting
 TelsyMobileDefender users will have reports generated by the platform from events tracked within the system.
TelsyMobileDefender users will have reports generated by the platform from events tracked within the system.
The report data will concern:
- Administrator user accesses to the platform;
- Applications, such as logs related to apps;
- Security, such as related to security warnings;
- Actions log, such as logs related to actions initiated on devices (e.g., swipe, update, upgrade, patching, etc.).
Learn more about this and other cyber solutions from Telsy
