Enhancing Healthcare Cybersecurity – TelsyMediSOC

In an industry where a vulnerability can lead to financial losses and to potentially life-threatening incidents, being prepared to defend against cyber threats becomes imperative.
In this context, healthcare organizations are favorite targets for malicious actors and cybercriminals, due to the intrinsic high value of the data they produce, as well as the thriving Dark Web marketplace.
Healthcare: a favorite target for cybercriminals
The healthcare sector faces a myriad of cyber attacks, making it even more susceptible than other industries.
Let’s explore some of the reasons behind this concerning trend.
Embracing the digital revolution – By 2030, the Healthcare sector, along with BFSI and Manufacturing, is expected to undergo a significant digital transformation, leading to an increased cyber risk associated with the adoption of cutting-edge technologies.
The intrinsic value of medical data – The value of medical data can surpass the one of banking or credit card information by up to 20 times. Consequently, healthcare infrastructure is particularly vulnerable to ransomware attacks.

The rise of IoT – As the utilization of connected devices within healthcare facilities continues to soar, the sector becomes increasingly exposed and susceptible to cyber threats from malicious hackers.
Easy entry points – Medical devices, while not directly carrying sensitive data, serve as critical gateways into hospital networks and are often easily compromised by hackers. They lack the dedicated security layers found in laptops or computers.
Exposed information – In a “time-critical” industry where sensitive data is extensively shared, devices with unprotected access offer lucrative opportunities for malicious actors.
Mitigating the human factor – Healthcare workers often lack basic knowledge about online security, inadvertently becoming a primary cyber risk. Empowering them through targeted security awareness pathways can be very effective.
Addressing outdated technology – Budget constraints and reluctance to adopt new technologies often result in the use of outdated or end-of-life software that carries critical vulnerabilities.
Securing remote access – Collaboration, even across remote or distant locations, plays a pivotal role in the healthcare sector. Therefore, monitoring the identity and origin of remote access becomes crucial in preventing data breaches.
No organization is immune – Even small and mid-sized healthcare organizations cannot afford to neglect security issues. They are prime targets for hackers who rely on their often inadequate or outdated defensive measures.
Value and trends of attacks on the Healthcare sector
According to Sole 24Ore, the value of a single health record on the Dark Web is today around $2,000, up to 20 times higher than data extracted from credit cards.
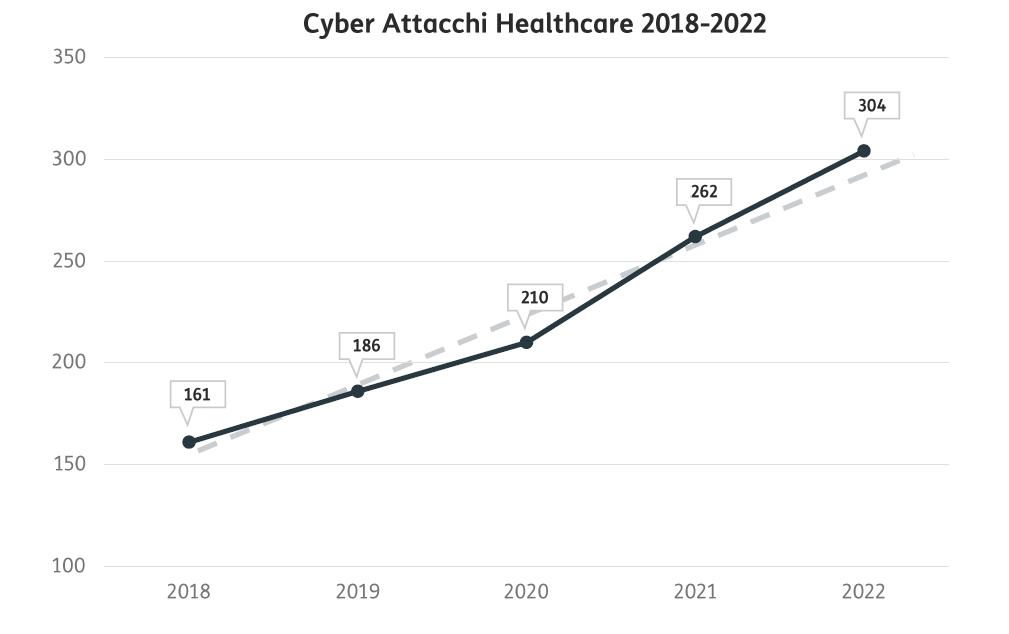
In 2022, in Italy, there was further growth in cyber attacks on the Healthcare sector, almost double from just 4 years ago (2023 Report on ICT Security in Italy, Clusit).
And also in 2022, in Italy, the Healthcare sector was the most affected by cyber attacks with more than 70% of attacks having a severe (46%) or very severe (25%) impact.
To reduce the level of exposure to cyber risk, there is a need for hospitals and health organizations to implement a system of technologies capable of responding, predicting and anticipating, cyber attacks through the use of intelligence systems, hopefully combined with the expertise of a 24/7 security operations center (SOC).
TelsyMediSOC – the Healthcare organizations’ cybersecurity solution
TelsyMediSOC is the Healthcare cybersecurity solution managed by Telsy’s iSOC that provides customers with a responsive and proactive cyber risk monitoring tool within healthcare infrastructure.

Provides, for all types of devices in the healthcare facility (IT, OT, loT and MIoT), constant protection against different types of attacks, including ransomware, malware and data exfiltration.
The analytical dashboard on device utilization enables optimal management of device distribution across sites and reduces the period of idle devices.
In addition, the “Patient Safety,” “Patient Confidentiality,” and “Service Disruption” indices enable the proper prioritization of remediation actions.
TelsyMediSOC is designed to connect with SIEM, SOAR, Firewall, NAC, RTLS technologies, and other health IT and security systems.
It enables micro-segmentation of devices through the creation, testing and implementation, also automated, of policies for device protection, as well as immediate and reactive identification and remediation to “live” attacks occurring on connected devices.
Key Features of TelsyMediSOC
In a time-critical industry such as Healthcare, entrusting technology management to Telsy’s iSOC professionals allows each organization to fully devote itself to day-to-day activities avoiding wasting resources on labor-intensive security activities.
The TelsyMediSOC service consists of 3 main functionalities:
Asset lnventory & Visibility
It allows 3 different views:
“Card” view – Provides a view of assets grouped by type and associates, for each type, the associated risk level through a color bar.
View by device – Provides a view by individual device, with specific information of various kinds, including associated risk level, connection map and usage statistics.
View by group – For each device type, provides a specific list of devices with detailed summary information for each.
Risk ldentification
Consists of 4 interoperating elements:
Risk Heatmap – Provides a view of risks based on the potential impact in terms of Patient Safety, Information Confidentiality, and Service Disruption.
Device Utilization – Provides graphs and views regarding the degree of device utilization, by group and by individual device, to support optimal device deployment decision making.
Risk Map – Provides a view that associates the vulnerability exploitation probability with the associated potential impact.
Risk Classification – Provides a summary dashboard of all identified and suspected risks as well as mitigated and inactive risks.
Mitigation, Detection & Response
Functionality includes 4 distinctive features:
Security Posture – General view of the organization’s security score and mitigation suggestions by device type.
Forensic Investigation Support – Detail view of the detected threat and drill down on the entire attack kill chain.
Critical Alerts and Immediate Response – Upon detection of critical anomalies, detailed information on the detected threat and immediate response actions are provided.
Quick Wins – Suggestions on immediate mitigation actions for improving the security posture, based on Security (e.g. E-W Segmentation), Biomed (e.g. Firmware Update) or Executive.
Learn more about this and other cyber solutions from Telsy on our website.
