BabaDeda and LorecCPL downloaders used to run Outsteel against Ukraine
Telsy CTI Team found and followed insights from the Ukraine question, new IoCs, and the evolution of the tools employed in the attacks.
Beginning in January 2022, there was a series of attacks on numerous organizations in Ukraine spanning the government, the military, non-governmental organizations (NGOs), with the primary intent of exfiltrating sensitive information and maintaining access.
Based on these new details and Telsy‘s threat hunt, we uncovered several links that strongly support the idea that these attacks were part of a larger campaign that has been running for a few months and has undergone several evolutions.
In this way, we have mapped the various clusters and in particular three chains of infection, composed of a series of techniques and procedures, with several significant elements that we consider important to better understand the various phases implemented.
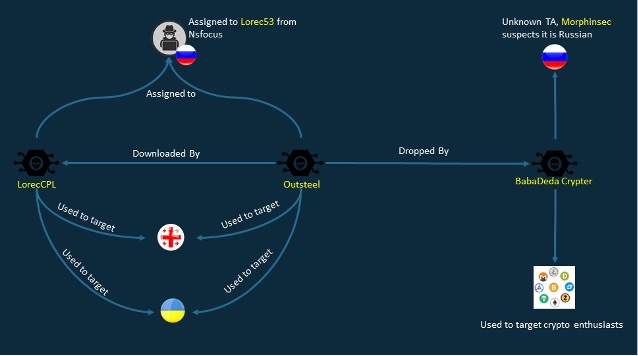
One of the most used access vectors in these campaigns is spear-phishing emails with malicious attachments. Phishing attachments contain a first-stage payload that downloads and executes additional payloads. The main payload provided by the malware is an infostealer written in AutoIt compiled (OutSteel). Its main goal is to steal files from the victim’s machine by uploading them to a default Command and control (C2) server. The element detected in these latter chains is the downloader used to load the infostealer “Outsteel”. In the past, this was loaded by the SaintBot tool while in these campaigns, it is loaded by the BabaDeda crypter.
Based on victimology and the fact that this attack attempts to steal files from government entities, it is assumed to be a state-sponsored group.
Some evidence suggests that these activities are carried out by a hacker group called “Lorec53” as named by the security firm “NSFocus”. The group is suspected of being employed by other high-level espionage organizations to conduct espionage attacks, targeting government employees in Georgia and Ukraine. This group uses the infostealer “Outsteel” and the downloader “LorecCPL“, both of which have overlapping code with the same artifacts identified in the campaigns analyzed in this report. We can therefore assume that the BabaDeda crypter is also one of the tools in use by this group.
Fill out the form below to download the full report
[email-download download_id=”6372” contact_form_id=”4482”]
Check other cyber reports on our blog.
This report was produced by Telsy’s “Cyber Threat Intelligence” team with the help of its CTI platform, which allows to analyze and stay updated on adversaries and threats that could impact customers’ business.
