Simjacker and other cyber threats for mobile devices in 2020
At the end of last year, a security company discovered a serious threat to the world of cell phones and beyond: Simjacker, an attack technique that allows, in fact, to take control of a mobile phone by simply sending an SMS. Given the always increasing use of smartphones, it’s easy to understand the great dangerousness of this type of attack. Here we will see some details about this and other cyber threats for mobile devices that have recently emerged.
Simjacker, the first case of Malware-SMS
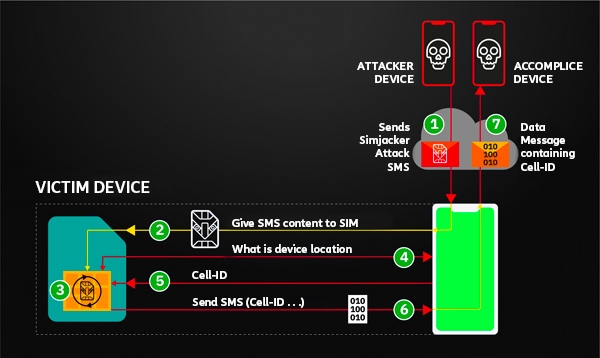
The Simjacker technique is particularly dangerous because it can be successfully exploited against a large variety of connected devices: not only mobile phones and smartphones, but also IoT devices that require the presence of a SIM card inside of them. It is a “platform-agnostic” attack (which means that it doesn’t depend on a specific type of hardware or software) and the victim can do almost nothing to defend himself against this threat, especially because the attack is completely transparent to the user who cannot in any way notice that he has become a target.
The principle on which this technique is based it’s quite simple: it’s sufficient to send a specially formatted SMS containing precise instructions, in order to open a direct communication channel with the SIM card, which will respond to the message by sending the IMEI code and the location relative to the cell to which the device is connected. The user is unable to notice any anomaly because there is no trace of these operations on the SMS log. The attack is made possible by the S@T Browser software – a contraction of the SIMalliance Toolbox Browser – which has been defined by the SIM Alliance and is installed on a wide variety of SIM Cards including eSIMs. It is a small software, originally meant to provide specific services to users by network operators.
According to the security company, in most cases the purpose of the attack was to trace the geographical position of the device, with the transmission of the unique IMEI code. It should be noted, however, that in fact the technique can allow you to take control, in a more or less profound way, of the targeted device. The fact that Simjacker can issue a list of instructions makes it the first real case of malware / spyware delivered directly via SMS. In all previous cases, the spread of malware via SMS always involved sending a link, not the malicious software integrated into the message itself.
Some of the other threats to mobile security in 2020
In addition to Simjacker, several other threats to mobile devices have emerged in recent times. showing that they are becoming the favourite targets of many cybercriminal groups. Recent research has also found that hackers have significantly expanded ways of hiding their attacks, making them increasingly difficult to identify and remove, suggesting that 2020 will be the year of stealthy mobile attacks.
The hidden apps
Hidden apps are the most prevalent mobile threat, generating almost 50% of all malicious activities in 2019, an increase of 30% over 2018. These malicious applications are designed to avoid being detected on the device once installed and are therefore extremely difficult to remove.
The main objective of these applications is to generate money for the attacker, often by downloading apps and automatically clicking on the background advertising links or by constantly bombarding the user with pop-up ads that they cannot get rid of.
Social engineering and gaming
A criminal tactic that works better on mobile devices than on the desktop is social engineering. In fact, due to the small screen size, many mobile email clients only display the sender’s name and it’s mainly for this reason that mobile users are three times more likely to be victims of a phishing attack than desktop users.
Hackers are also exploiting the popularity of online gaming to distribute their malicious apps via links diffused through the most popular chats and video platforms. These apps disguise themselves as authentic with icons that closely mimic those of the real apps, and then spread unwanted ads and collect user data.
Cryptojacking
Cryptojacking is a type of attack in which a cybercriminal uses a device to extract cryptocurrencies without the owner’s knowledge. It was born on the desktop, saw a surge on mobile devices between the end of 2017 and the beginning of 2018. You realize that you are a victim because the autonomy of the smartphone drops drastically, moreover this malware often causes overheating of the components that can also physically damage the device.
The right approach to solve these security issues
All these new threats to mobile devices must make us reflect on what is the right approach to take in the IT security sector. Security is in fact a process whose strength is equal to that of the weakest link in its chain. Although often the weakest link is the end user (who is targeted in many ways, all the result of the most sophisticated and refined social engineering techniques), sometimes it happens, as in the case of Simjacker, that the weakest link in the chain is totally beyond the control of the end user.
It is for this reason that the security by design approach must be the key priority in the world of technological development: think first about the security of a system (whether it is a technology, a software or a device) and only afterwards to its functionality.
With this in mind, a great collaborative effort is needed from all the actors involved (companies, public, private, research) in order to build an ecosystem composed of knowledge, skills, solutions, procedures that can lead to a continuous and effective risk management, able to adapt more and more readily to the constantly changing threats that are putting the security of all devices at risk.
