Leon Battista Alberti’s cipher disk

Leon Battista Alberti’s cipher disk, described in “De cifris” around 1467, is the first polyalphabetic encryption system.
The device consists of two concentric discs, rotating relative to each other, containing an alphabet ordered for the plain text (text to be encrypted) and a “disordered” alphabet for the cipher text (resulting text).
Allows polyalphabetic substitution with irregular periods. Scrolling of the alphabets occurs using key letters inserted in the body of the cryptogram.
The four numbers can also be used to overcode 336 code phrases.
The story of Leon Battista Alberti
Leon Battista Alberti (1404 – 1472) was an Italian architect, writer, mathematician, humanist, cryptographer, linguist, philosopher, musician, and archaeologist; he was one of the most multifaceted artistic figures of the Renaissance.

Alberti is part of the second generation of humanists (the one following Vergerio, Bruni, Bracciolini, and Francesco Barbaro), of which he was an emblematic figure for his interest in the most varied disciplines.
A constant Alberti’s interest was the search for rules, theoretical or practical, capable of guiding the work of artists.
As an architect, Alberti is considered, alongside Brunelleschi, the founder of Renaissance architecture.
The innovative aspect of his proposals, especially in both the architectural and humanistic fields, consisted in the modern reworking of the ancient, sought as a model to emulate and not simply to replicate.
Leon Battista Alberti and cryptography
Alberti was also a brilliant cryptographer and invented a method to generate encrypted messages with the help of an already mentioned device: the encrypting disk.
Indeed, his idea was to pass from cryptography with a “monoalphabetic” technique (like the Caesar Cipher) to one with a “polyalphabetic” technique, theoretically codified several years later by Blaise de Vigenère.
In “The Codebreakers. The Story of Secret Writing”, the historian of cryptology David Kahn attributes to Alberti the title of Father of Western cryptology.
The encrypting disk
Leon Battista Alberti, at the end of his Trattato sulla cifra, writes:
Nunc de scribendi ratione a nobis inuenta dicendum sequitur. Habet ea quidem has commoditates, nulla omnium qua quis uti possit cyfra expeditior: nulla scribitur commodius, nulla ubi ex instituto modum teneas, promptius apreusque legitur […].
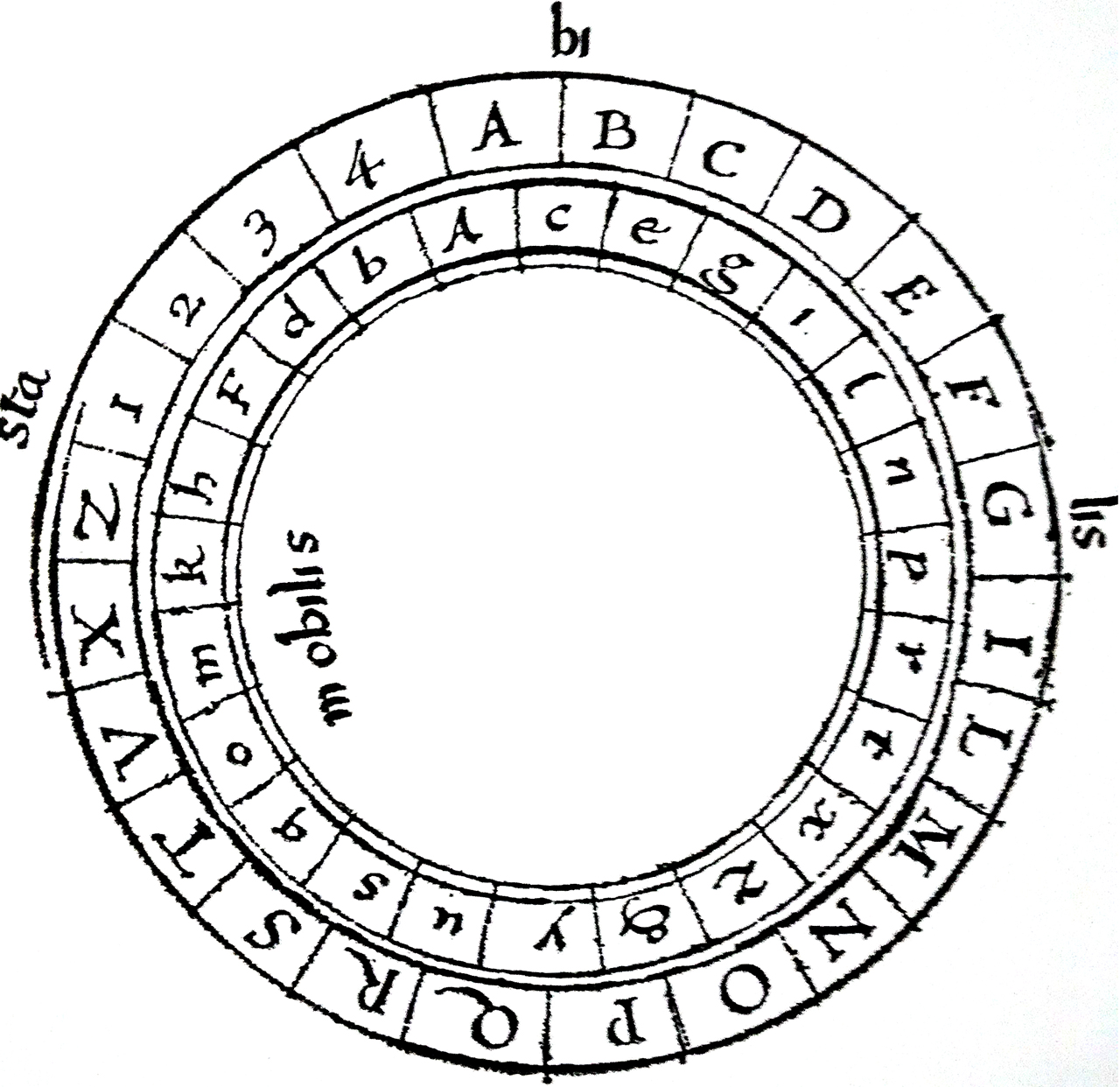
Alberti, therefore, proposes several figures that make use of the same instrument, a double-disc, which Alberti calls formula, formed by two concentric circles of bronze or other material.
The external one, called stable, with 24 boxes containing, in red uppercase, ordered, the 20 letters of the Latin alphabet, with the Z (ABCDEFGILMNOPQRSTVXZ) and excluding the rare H, K (J, U, W, Y were not part of the classic Latin alphabet), followed by the numbers 1 2 3 4 for the clear text.
The inner one, called mobile, with 24 lowercase letters in black in random order, messy. This norm of disorder is fundamental; otherwise we have a figure of Caesar or Vigenère.
Procedures for encrypting and decrypting
By keeping the internal disk in a fixed position, it creates a monoalphabetic cipher list with the number 1,2,3,4 as null.
The three encryption methods proposed by Alberti in his treatise are more sophisticated and secure:
 First case
First case
The two correspondents, Alice and Bob, agree on a lowercase letter, for example, k as the secret key; the sender rotates the movable disk up to bring k under a capital letter, for example B, which is written as the first letter of the cipher, after which a few letters are encrypted with the resulting list, then the internal disk is rotated randomly by some positions, getting a new list.
The change of list is signaled by writing the capital letter under which the k is now found, and so on with each list change.
Example: if you want to encrypt the message ” INVIARE RINFORZI DOMANI “, some nulls are inserted at random, then encrypted by changing the list, always at random, 3 times:
clear INVIARERINFORZIDOMANI
with null INV1IA R2ERI4NF1O RZID 3OMANI
encrypted BeghyeoLeiqeolpcafPpmylZfhrsla
The decryption proceeds in reverse: the recipient reads at the beginning of the cipher B, brings k under B and decrypts with this list up to the next capital letter; then he puts k under that uppercase and decodes the following characters according to the new list up to the next uppercase and so on.
Security is therefore based, in addition to the lowercase letter, also and above all on the internal disk, the disordered one, which is part of the key: Alice and Bob must have two identical copies and if they want to change the key they must make another one, otherwise messy.
Second case
Capital letters, however, are helpful not only for the correspondent but also for the enemy: to increase security Alberti suggests using a capital letter as a key, for example B, and writing the corresponding lowercase at the beginning of the message and using then the four digits no longer as null but to signal the change of alphabet; the lower case letter corresponding to the number will be the new key and will be brought under B; the previous example then becomes:
clear INVIARERINFORZIDOMANI
with numbers INVIA1RERINFO4RZID2OMANI
encrypted kegheoydjdbzosnetoyiocajy
 The cipher coincides with the previous one only at the beginning; there are no more capital letters; the decryption proceeds as above: the recipient brings the first letter k to coincide with B and decrypts with this list until he gets the number 1, in this example at the y; then he rotates the disk until y coincides with B and so on until he finds another digit. Alternatively, you could use a single digit as a list change symbol, and the other 3 as null.
The cipher coincides with the previous one only at the beginning; there are no more capital letters; the decryption proceeds as above: the recipient brings the first letter k to coincide with B and decrypts with this list until he gets the number 1, in this example at the y; then he rotates the disk until y coincides with B and so on until he finds another digit. Alternatively, you could use a single digit as a list change symbol, and the other 3 as null.
Third case
At the end of the treatise, Alberti proposes a completely different system, encoding by phrases instead of by words: at the base there is a phrasebook of common messages encrypted with only 4 digits (1,2,3,4) present on the disk; the two-digit numbers from 11 to 44 are 16, those of 3 digits from 111 to 444 are 64, those of 4 digits from 1111 to 4444 are 256, in all 336 combinations which therefore allow a rather full-bodied phrase book.
To make it even broader, Alberti proposes to create many lists distinct by topic from a capital letter, for example A for annona, B for war events, etc. etc. then to use the disc to substitute the numbers with the letters below in the rotated disc to an agreed position. Consisting of two passages it could be considered a form of over-encryption, but in fact, it boils down to one digit where each sentence is encrypted with a group of two to four letters; at the end of the treaty there is an empty list, to be filled in, of the possible figures from 11 to 4444; there is no complete usage example.
Security of the encrypting disk
As stated above, security is mostly based on the internal disk which is a permutation of the 24-letter alphabet.
One flaw is that by its nature this key cannot be held by heart, and the disk must be kept in a safe place.
The use of the disk is not so convenient, and if it is necessary to change the key, it is necessary to make a new one.
Certainly, the two systems described by Alberti are safer than many later figures.
