Recent “CEO Fraud” campaign is spreading within EU and already made victims. Telsy TRT joined an international collaborative effort for researching and mitigating the threat.
In the first days of May 2019, Telsy TRT joined a collaborative international effort aimed at studying, researching and mitigating a recent malicious campaign carried out by a criminal gang we internally track as #TA-927. Our collaboration has mainly seen, among others, Theo Geurts as an active member of the ICANN community . He has been an essential part of our mitigation efforts. According to Wikipedia, ICANN is the organization responsible for coordinating the maintenance and procedures of several databases related to the namespaces and numerical spaces of the global Internet network.
The “CEO Fraud” attempts are not uncommon. Recently, an italian organization has been hit by a similar attack. Following, we report an article by corriere.it [an italian magazine] describing the fraud suffered recently by Tecnimont:
https://milano.corriere.it/19_giugno_11/tecnimont-truffata-mail-capo-era-falsa-persi-17-milioni-euro-a36e5f20-8c7e-11e9-9a2c-4fa09850aca0.shtml
Insight
In accordance with some technical evidences extracted in addition to the use of online russian services, the members of the group operating this campaign are probably russian speakers (or at least some of them).
In the analysis of the infrastructures and some pieces of likely related malware, we noted recursive technological patterns that have led us to associate some different malicious activities to the same criminal organization.
The campaign under analysis, aimed at scams and network intrusions dedicated to economic and financial gain, is spreading around some countries of the european area involving entities from Italy as well.
The actor operates through different methods and we observed that in special cases it goes directly to target high-level personnel belonging to the financial divisions of the companies it intends to defraud.
The attack usually is carried out through targeted email reporting alleged problems with acquisitions and / or financial transitions in place or planned for the immediate future.
In some cases the emails go to target different people within the same organization. The malicious communication, usually addressed at senior company’s financial officers, goes to impersonate the CEO in order to instill a sense of urgency and absolute priority about the requests received.
OSINT insights conducted during the study phases of the threat confirmed the roles and names of all identities that the actor attempted to impersonate. This goes to confirm us a meticulous information gathering activity towards the companies against which the operations are conducted.
The malicious campaign, commonly named “CEO Fraud”, probably began at the beginning of March 2019. However, some subsequent correlations conducted on the malicious infrastructure made it possible to date the group’s activities back at least a year ago.
With a number of domain names attributable to the same actor of no less than 200 units and active manteinance of some pieces of malware over time, it is possible to confirm with a high degree of confidence the organized nature of the threat in question.
It seems to operate mainly through different methods to reach their scope:
- %COMPUTERNAME%
- %USERNAME%
- %os%
- %cpu%
- %NUMBER_OF_PROCESSORS%
- %gpu%
They are all sent outside with a command line similar to the following:
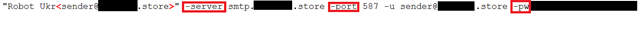
The miner is using the CryptoNight algorithm to mine the monero cryptocurrency. As mentioned, its spread prevails in the russian region and in the Countries of Eastern Europe.
We identified several variants of the same malware families. Some of them add some features to the base root but the exfiltration and communication channel remains based on SMTP protocol while the set of information sent outside may vary.
Exploding the Infrastructure
As reported earlier, the infrastructure under analysis appears to be a very large one. We counted at least 200 registered domain names and some of them have been setted up very recently confirming we have in front a still active threat. The actor seems to perform the tuning of his infrastructure on the basis of what the future goals are, maintaining a good logical level in the separation of the same between actions aimed at scam and/or fraud with those aimed at malware spreading / installation.
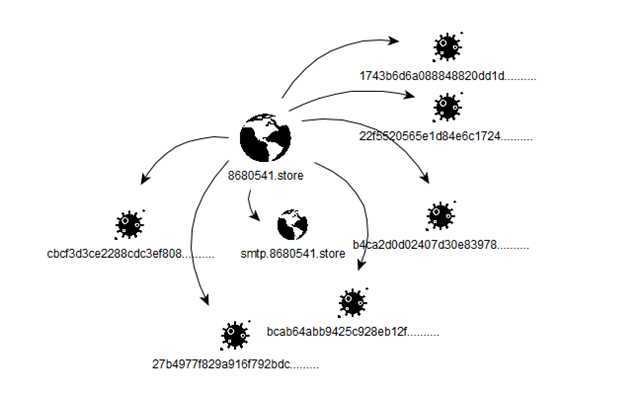
Starting from the correlations carried out, it is possible to further explode the individual entities of the graph by going into detail on the individual aspects of a single malicious asset in question.
The following graph represents a correlation of elements between a single entity dedicated to the spread of malware and some of these to be associated with it:
Conclusion
Cyber criminal groups are often very organized and determined to achieve their goals. Behind a simple email used in attempt to fraud companies and/or institutions, there can be organizations with a very large and structured infrastructure capable to fully serve their malicious intent.
As observed, these groups often move in multiple directions, sometimes re-using infrastructures already observed, sometimes setting up new infrastructures within a few days; this much depends on their goals. The group under examination is clearly oriented towards fund raising campaigns, targeting small and large entities through different ways. Social engineering may be an under-estimate threat. The recommendations that can be issued in these cases range from the adoption of behaviors aimed at verifying the origin of communications (email, phone, social, chat etc.etc.) as well as the use of internal training aimed at the awareness of the staff regarding these possible ways to achieve frauds and network intrusions.
Indicators of Compromise
corp-cell01.com
phone-personalceo.com
internal-mob01.com
8680541.store
office-firma.store
Further IoCs can be exchange for free with entitled parties.
For other related articles, check our blog.
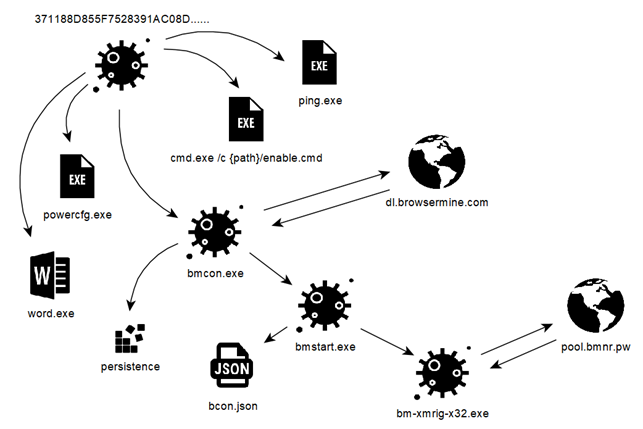
enable.cmd provides the first system configurations and the starts the executable sender.exe. sender.exe is able to handle some startup parameters given as input; the values of these parameters are collected by enable.cmd itself and sent to the outside through SMTP communications.
The exaustive list of retrieved information is reported below:
- %COMPUTERNAME%
- %USERNAME%
- %os%
- %cpu%
- %NUMBER_OF_PROCESSORS%
- %gpu%
They are all sent outside with a command line similar to the following:

The miner is using the CryptoNight algorithm to mine the monero cryptocurrency. As mentioned, its spread prevails in the russian region and in the Countries of Eastern Europe.
We identified several variants of the same malware families. Some of them add some features to the base root but the exfiltration and communication channel remains based on SMTP protocol while the set of information sent outside may vary.
Exploding the Infrastructure
As reported earlier, the infrastructure under analysis appears to be a very large one. We counted at least 200 registered domain names and some of them have been setted up very recently confirming we have in front a still active threat. The actor seems to perform the tuning of his infrastructure on the basis of what the future goals are, maintaining a good logical level in the separation of the same between actions aimed at scam and/or fraud with those aimed at malware spreading / installation.
Starting from the correlations carried out, it is possible to further explode the individual entities of the graph by going into detail on the individual aspects of a single malicious asset in question.
The following graph represents a correlation of elements between a single entity dedicated to the spread of malware and some of these to be associated with it:

Conclusion
Cyber criminal groups are often very organized and determined to achieve their goals. Behind a simple email used in attempt to fraud companies and/or institutions, there can be organizations with a very large and structured infrastructure capable to fully serve their malicious intent.
As observed, these groups often move in multiple directions, sometimes re-using infrastructures already observed, sometimes setting up new infrastructures within a few days; this much depends on their goals. The group under examination is clearly oriented towards fund raising campaigns, targeting small and large entities through different ways. Social engineering may be an under-estimate threat. The recommendations that can be issued in these cases range from the adoption of behaviors aimed at verifying the origin of communications (email, phone, social, chat etc.etc.) as well as the use of internal training aimed at the awareness of the staff regarding these possible ways to achieve frauds and network intrusions.
Indicators of Compromise
corp-cell01.com
phone-personalceo.com
internal-mob01.com
8680541.store
office-firma.store
Further IoCs can be exchange for free with entitled parties.
For other related articles, check our blog.
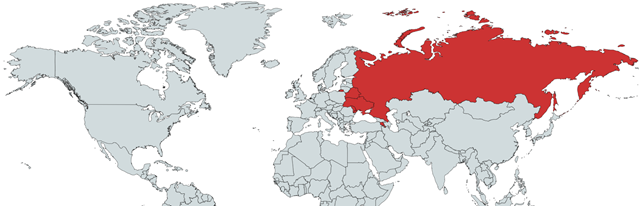
The use of crypto mining malware was instead observed mainly in the east-countries region, including Russia:
Miner details
The miner malware is spreading through self-extracting archives or executable files with .scr extension.
In the latter case, a version of the SIM packer (5.02) is used to assemble and compress the set of malicious components to be installed and to be runned on the system.
In order to extract the total of the malicious files present in the whole SIM protected blob, we have written a few lines of code in order to extract the configuration files and the contents for a better understanding of the actions performed.
Following an image with the exaustive list of components retrieved from the installer configuration file:

bmcon.exe, copied as protected file system, is normally invisible browsing the folder using windows explorer. It’s the principal loader of further malicious components that will go to provide for the mining workload.
Following a simplified model about how the payload is exploded into the system:

enable.cmd provides the first system configurations and the starts the executable sender.exe. sender.exe is able to handle some startup parameters given as input; the values of these parameters are collected by enable.cmd itself and sent to the outside through SMTP communications.
The exaustive list of retrieved information is reported below:
- %COMPUTERNAME%
- %USERNAME%
- %os%
- %cpu%
- %NUMBER_OF_PROCESSORS%
- %gpu%
They are all sent outside with a command line similar to the following:

The miner is using the CryptoNight algorithm to mine the monero cryptocurrency. As mentioned, its spread prevails in the russian region and in the Countries of Eastern Europe.
We identified several variants of the same malware families. Some of them add some features to the base root but the exfiltration and communication channel remains based on SMTP protocol while the set of information sent outside may vary.
Exploding the Infrastructure
As reported earlier, the infrastructure under analysis appears to be a very large one. We counted at least 200 registered domain names and some of them have been setted up very recently confirming we have in front a still active threat. The actor seems to perform the tuning of his infrastructure on the basis of what the future goals are, maintaining a good logical level in the separation of the same between actions aimed at scam and/or fraud with those aimed at malware spreading / installation.
Starting from the correlations carried out, it is possible to further explode the individual entities of the graph by going into detail on the individual aspects of a single malicious asset in question.
The following graph represents a correlation of elements between a single entity dedicated to the spread of malware and some of these to be associated with it:

Conclusion
Cyber criminal groups are often very organized and determined to achieve their goals. Behind a simple email used in attempt to fraud companies and/or institutions, there can be organizations with a very large and structured infrastructure capable to fully serve their malicious intent.
As observed, these groups often move in multiple directions, sometimes re-using infrastructures already observed, sometimes setting up new infrastructures within a few days; this much depends on their goals. The group under examination is clearly oriented towards fund raising campaigns, targeting small and large entities through different ways. Social engineering may be an under-estimate threat. The recommendations that can be issued in these cases range from the adoption of behaviors aimed at verifying the origin of communications (email, phone, social, chat etc.etc.) as well as the use of internal training aimed at the awareness of the staff regarding these possible ways to achieve frauds and network intrusions.
Indicators of Compromise
corp-cell01.com
phone-personalceo.com
internal-mob01.com
8680541.store
office-firma.store
Further IoCs can be exchange for free with entitled parties.
For other related articles, check our blog.
- [organization name]-login.site
- sso-[organization].site
- [organization name]-portal.site.
It’s lecit to believe that such malicious actions may lead to the acquisition of further information regarding the victim company (in addition to those normally available through web searches), which could be used to support further operations against to the same target or to third parties entities.
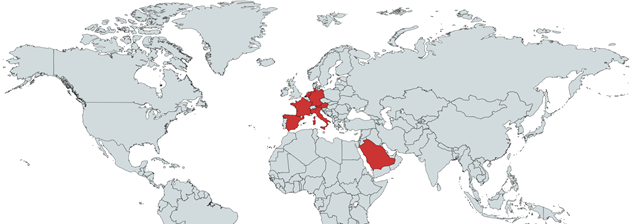
Social engineering tricks has been observed mainly against central EU companies / organizations with some cases aimed at companies operating in Saudi Arabia. The following is an exhaustive representation of where Telsy TRT is observing this kind of activities:

The use of crypto mining malware was instead observed mainly in the east-countries region, including Russia:

Miner details
The miner malware is spreading through self-extracting archives or executable files with .scr extension.
In the latter case, a version of the SIM packer (5.02) is used to assemble and compress the set of malicious components to be installed and to be runned on the system.
In order to extract the total of the malicious files present in the whole SIM protected blob, we have written a few lines of code in order to extract the configuration files and the contents for a better understanding of the actions performed.
Following an image with the exaustive list of components retrieved from the installer configuration file:

bmcon.exe, copied as protected file system, is normally invisible browsing the folder using windows explorer. It’s the principal loader of further malicious components that will go to provide for the mining workload.
Following a simplified model about how the payload is exploded into the system:

enable.cmd provides the first system configurations and the starts the executable sender.exe. sender.exe is able to handle some startup parameters given as input; the values of these parameters are collected by enable.cmd itself and sent to the outside through SMTP communications.
The exaustive list of retrieved information is reported below:
- %COMPUTERNAME%
- %USERNAME%
- %os%
- %cpu%
- %NUMBER_OF_PROCESSORS%
- %gpu%
They are all sent outside with a command line similar to the following:

The miner is using the CryptoNight algorithm to mine the monero cryptocurrency. As mentioned, its spread prevails in the russian region and in the Countries of Eastern Europe.
We identified several variants of the same malware families. Some of them add some features to the base root but the exfiltration and communication channel remains based on SMTP protocol while the set of information sent outside may vary.
Exploding the Infrastructure
As reported earlier, the infrastructure under analysis appears to be a very large one. We counted at least 200 registered domain names and some of them have been setted up very recently confirming we have in front a still active threat. The actor seems to perform the tuning of his infrastructure on the basis of what the future goals are, maintaining a good logical level in the separation of the same between actions aimed at scam and/or fraud with those aimed at malware spreading / installation.
Starting from the correlations carried out, it is possible to further explode the individual entities of the graph by going into detail on the individual aspects of a single malicious asset in question.
The following graph represents a correlation of elements between a single entity dedicated to the spread of malware and some of these to be associated with it:

Conclusion
Cyber criminal groups are often very organized and determined to achieve their goals. Behind a simple email used in attempt to fraud companies and/or institutions, there can be organizations with a very large and structured infrastructure capable to fully serve their malicious intent.
As observed, these groups often move in multiple directions, sometimes re-using infrastructures already observed, sometimes setting up new infrastructures within a few days; this much depends on their goals. The group under examination is clearly oriented towards fund raising campaigns, targeting small and large entities through different ways. Social engineering may be an under-estimate threat. The recommendations that can be issued in these cases range from the adoption of behaviors aimed at verifying the origin of communications (email, phone, social, chat etc.etc.) as well as the use of internal training aimed at the awareness of the staff regarding these possible ways to achieve frauds and network intrusions.
Indicators of Compromise
corp-cell01.com
phone-personalceo.com
internal-mob01.com
8680541.store
office-firma.store
Further IoCs can be exchange for free with entitled parties.
For other related articles, check our blog.
- Spear-phishing email oriented to have a first contact with the victim and potentially to steal useful information about accounts and financial flows related to the target.
- Spear-phishing emails aimed at acquiring useful service credentials of victims and potentially at installing malicious reconnaissance software within the victim system.
- Hacking of perimeters or exposed services [or combination including all of above] aimed at installing cryptocurrency mining malware.
In the first case, the targeted victim receives an email similar, in the body, to the following text:
From: [spoofing CEO email]
To: [CFO or high financial division officer]
“Good Morning [name], i need you to manage an high priority situation that is a prime concern deal for the group. [….redacted….] First of all [name], provide me the available cashflow of our bank account in [country]. Also, give me a phone number which on you are confortable to talk. As soon i receive those information, I will share with you further instructions. [CEO Name] [CEO Signature]”
In the second case, the actor uses social engineering techniques to convince the victim to enter its account / login credentials into fake online services that aim to replicate official authentication portals belonging to the company. In this case, very often, the malicious asset used goes to replicate domain names that can be similar to those used by the targeted organization, like, for example
- [organization name]-login.site
- sso-[organization].site
- [organization name]-portal.site.
It’s lecit to believe that such malicious actions may lead to the acquisition of further information regarding the victim company (in addition to those normally available through web searches), which could be used to support further operations against to the same target or to third parties entities.
Social engineering tricks has been observed mainly against central EU companies / organizations with some cases aimed at companies operating in Saudi Arabia. The following is an exhaustive representation of where Telsy TRT is observing this kind of activities:

The use of crypto mining malware was instead observed mainly in the east-countries region, including Russia:

Miner details
The miner malware is spreading through self-extracting archives or executable files with .scr extension.
In the latter case, a version of the SIM packer (5.02) is used to assemble and compress the set of malicious components to be installed and to be runned on the system.
In order to extract the total of the malicious files present in the whole SIM protected blob, we have written a few lines of code in order to extract the configuration files and the contents for a better understanding of the actions performed.
Following an image with the exaustive list of components retrieved from the installer configuration file:

bmcon.exe, copied as protected file system, is normally invisible browsing the folder using windows explorer. It’s the principal loader of further malicious components that will go to provide for the mining workload.
Following a simplified model about how the payload is exploded into the system:

enable.cmd provides the first system configurations and the starts the executable sender.exe. sender.exe is able to handle some startup parameters given as input; the values of these parameters are collected by enable.cmd itself and sent to the outside through SMTP communications.
The exaustive list of retrieved information is reported below:
- %COMPUTERNAME%
- %USERNAME%
- %os%
- %cpu%
- %NUMBER_OF_PROCESSORS%
- %gpu%
They are all sent outside with a command line similar to the following:

The miner is using the CryptoNight algorithm to mine the monero cryptocurrency. As mentioned, its spread prevails in the russian region and in the Countries of Eastern Europe.
We identified several variants of the same malware families. Some of them add some features to the base root but the exfiltration and communication channel remains based on SMTP protocol while the set of information sent outside may vary.
Exploding the Infrastructure
As reported earlier, the infrastructure under analysis appears to be a very large one. We counted at least 200 registered domain names and some of them have been setted up very recently confirming we have in front a still active threat. The actor seems to perform the tuning of his infrastructure on the basis of what the future goals are, maintaining a good logical level in the separation of the same between actions aimed at scam and/or fraud with those aimed at malware spreading / installation.
Starting from the correlations carried out, it is possible to further explode the individual entities of the graph by going into detail on the individual aspects of a single malicious asset in question.
The following graph represents a correlation of elements between a single entity dedicated to the spread of malware and some of these to be associated with it:

Conclusion
Cyber criminal groups are often very organized and determined to achieve their goals. Behind a simple email used in attempt to fraud companies and/or institutions, there can be organizations with a very large and structured infrastructure capable to fully serve their malicious intent.
As observed, these groups often move in multiple directions, sometimes re-using infrastructures already observed, sometimes setting up new infrastructures within a few days; this much depends on their goals. The group under examination is clearly oriented towards fund raising campaigns, targeting small and large entities through different ways. Social engineering may be an under-estimate threat. The recommendations that can be issued in these cases range from the adoption of behaviors aimed at verifying the origin of communications (email, phone, social, chat etc.etc.) as well as the use of internal training aimed at the awareness of the staff regarding these possible ways to achieve frauds and network intrusions.
Indicators of Compromise
corp-cell01.com
phone-personalceo.com
internal-mob01.com
8680541.store
office-firma.store
Further IoCs can be exchange for free with entitled parties.
For other related articles, check our blog.
